Call center fraud is the deliberate act of faking an identity in a phone call to access confidential information or take control of user accounts. It manifests in various forms, including phishing, account takeover, and card not present (CNP). To prevent bad actors from infiltrating your system, understand the common types of deceitful practices, invest in a phone system that can identify suspicious activities, and conduct training to handle emerging forms of fraud effectively.
Types of Call Center Fraud
Call centers are primary targets for scams because they are essentially receptacles of customer data. When agents are manipulated into giving information, fraudsters and scammers easily gain access to other personal information or drain financial accounts.
Customer service representatives must be familiar with different types of call center fraud so they’re able to deter it before it causes irreversible damage to customers’ privacy and company reputation.
Below are some of the popular types of call center fraud.
Voice Phishing
Phishing involves a fraudster sending an email that appears to come from a reputable organization. By posing as a legitimate company, they lure service representatives to divulge sensitive information, such as login credentials or credit card numbers. Voice phishing or vishing is a form of phishing that uses a telephone instead of an email to make unsuspecting individuals give confidential information.
Call center agents are trained to be friendly and courteous towards callers and accommodate requests. Naturally, they believe the people calling in are genuine customers needing assistance. Given this, some service representatives fall victim to this call center scam.
Account Takeover
Part of call center security is asking personal questions like the last four digits of one’s social security number or birth date to authenticate the identity of a caller. The initial step in account takeover, also known as ATO, involves the bad actor trying to know these pieces of personal information through various tactics, including scouring social media, buying stolen credentials off the dark web, or social engineering.
Once they know these details, scammers pose as legitimate customers and trick agents into giving them access to the user account or granting unauthorized transactions. When the account is taken over, bad actors will change account information to keep legitimate users locked out.
CNP
This type of fraudulent activity involves bad actors contacting call centers to buy products and services using stolen or dark-web-bought payment card information. Since call centers don’t require physically showing the card, fraudsters only need to present the name, card number, and three-digit card verification value to push through with the transaction.
Sometimes, the transaction lacks a live human agent altogether, as the hacker only interacts with the IVR system. This makes detection of fraudulent activities more difficult.
IVR Mining
Bad actors gather sensitive information through social media research or data breaches. They then contact a call center and use the IVR to validate the acquired information or complete the ones they’re missing. IVRs collect confidential information, such as card numbers or PINs, making them valuable targets of fraudsters. Once hackers get bank details or login credentials, they easily launch account takeovers and unauthorized transactions.
Network Jacks
Through social engineering, a fraudster may gain access to the call center, connect their device to the network, and collect sensitive information. Your network has been compromised if you notice new programs being installed or some unknown programs requesting access. In addition, you’ll see that your security solutions are removed.
Benefits of Training Agents to Identify Fraud
Call center agents are susceptible to psychological manipulation, giving away sensitive information to bad actors. This is why a large part of call center fraud prevention involves conducting fraud awareness training sessions. These are the benefits of effective training sessions:
- Reduced risk for financial loss: According to the Association of Certified Fraud Examiners (ACFE), fraud costs companies worldwide an estimated 5% of their annual revenues. Aside from the financial loss from attacks, organizations bleed money from the cost of investigating and resolving incidents and losing customers. By training agents to spot deceitful activities, you minimize fraud’s financial impact.
- Compliance with industry standards: If you’re in the financial industry, you must adhere to various regulations, including anti-money laundering, Know Your Customer, and Payment Card Industry Data Security Standard (PCI-DSS), which all require training employees on how to protect customer information.
- Improved customer trust: When customer service representatives follow robust security procedures, clients communicate with your business with confidence and peace of mind. This translates to repeat transactions and brand loyalty.
Tools for Identifying Fraud
Part of call center fraud prevention and awareness training is using tools to recognize suspicious activities. Fortunately, most voice-over-internet-protocol (VoIP) phone systems are already equipped with fraud identification capabilities. Maximize these features as you combat fraud in your communication operations:
This feature filters inbound calls and automatically warns agents about suspected spam calls after cross-checking the phone number in spam or robocall databases. Agents can then accept, reject, or send the call to the voicemail inbox. Call screening works hand in hand with call blocking, allowing you to decline calls from anonymous callers, specific phone numbers, and robocallers.
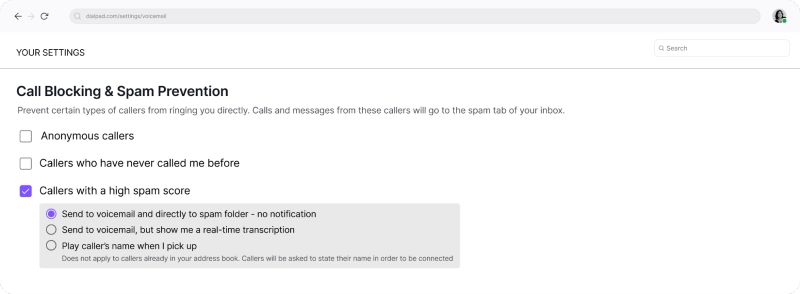
Screen and block callers with a high spam score on Dialpad. (Source: Dialpad)
VoIP phone system Dialpad screens inbound calls using spam scores and data from reliable third-party sources. Depending on your configuration, callers with a high spam score will be sent to voicemail or the spam folder with or without notification.
The call screening settings also include the option to prompt the caller to identify themselves before being connected to an agent. To know more about the platform’s features, read our comprehensive Dialpad review. The phone system’s entry-level subscription fee is $23 per user monthly. Maximize the fraud prevention solution call center’s 14-day free trial to access its features.
Reviewing call center activities regularly can reveal anomalies in calling patterns or IVR usage. For instance, multiple calls from a certain number during off-peak hours may suggest fraudsters testing out your IVR when you’re not actively monitoring the call center system.
To understand actual customer interactions better, refer to speech and voice analytics. Speech analytics examines the words spoken in a conversation while voice analytics studies the tone, pitch, and rhythm of the voice, giving insight into the call participants’ emotions.
As you check conversation transcripts and customer sentiments, look out for those who are having difficulty providing accurate personal information, insisting on updating contact details without verification, or intimidating you to share confidential data.
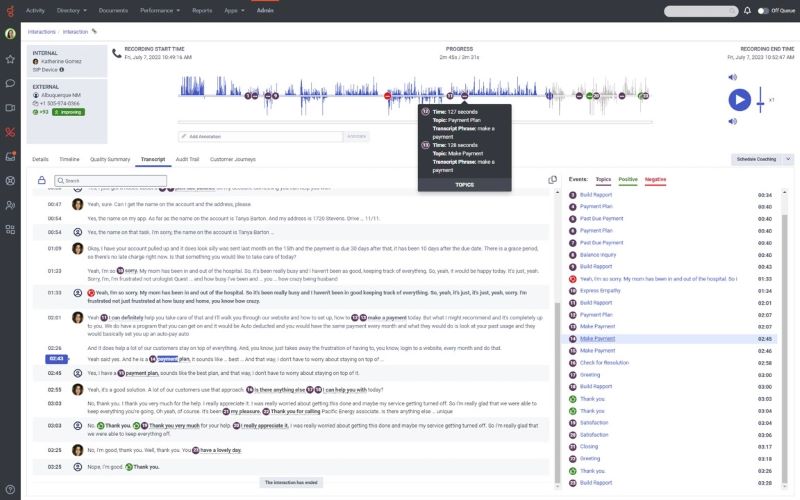
Analyze customer conversations on Genesys Cloud to spot fraudulent calls. (Source: Genesys)
Genesys Cloud features speech and voice analytics, providing a transcript and audio recording of the conversation. On the side panel, you’ll see the topics tackled in the phone call, along with the positive and negative words mentioned. Use this feature to determine if a customer demands changes in contact details or refuses to answer security questions.
If you’re interested in this platform, the starting fee is $75 per user monthly, and the subscription is billed annually.
Spoofing is the practice of using a false caller ID to disguise one’s identity. Fraudsters employ neighbor spoofing, where their phone number looks similar to local numbers in your area. This makes call recipients more likely to answer because they are familiar with the phone number.
Business phone systems use Secure Telephone Identity Revisited (STIR) and Signature-based Handling of Asserted Information Using toKENs (SHAKEN), a suite of protocols and procedures that implement caller ID authentication. With this technology, you’ll receive alerts when a caller is a spoofer.
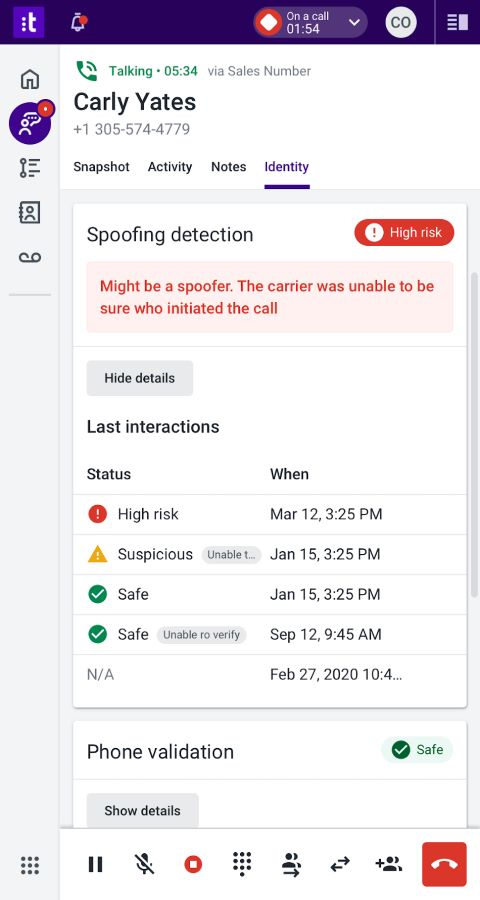
Immediately detect which inbound callers use number spoofing via Talkdesk. (Source: Talkdesk)
Talkdesk is a call center system that features spoof detection. It assigns three labels when examining a phone number:
- “Safe,” which means the carrier has fully authenticated that the calling customer is authorized to use the phone number;
- “Suspicious,” indicating that the service provider has verified its relationship with the calling customer but not the authorized use of the number;
- “High-risk,” meaning the carrier has authenticated that the call was on its network but has no relationship with the calling customer.
The platform has various call center fraud prevention services, including phone validation. Subscribe to the platform for only $85 per user monthly.
Advanced call center systems record voice samples, process pitch, tone, accent, and other voice features, and create a voiceprint or a digital representation of the voice’s unique characteristics. When a customer calls, the system automatically compares the live voice to the stored voiceprint and informs the agent if the identity is verified.
NICE CXone employs voice biometrics to authenticate caller identity. To activate the feature, you must enroll the contact in the system. During enrollment, the phone system records the phone number and creates the corresponding customer’s voiceprint.
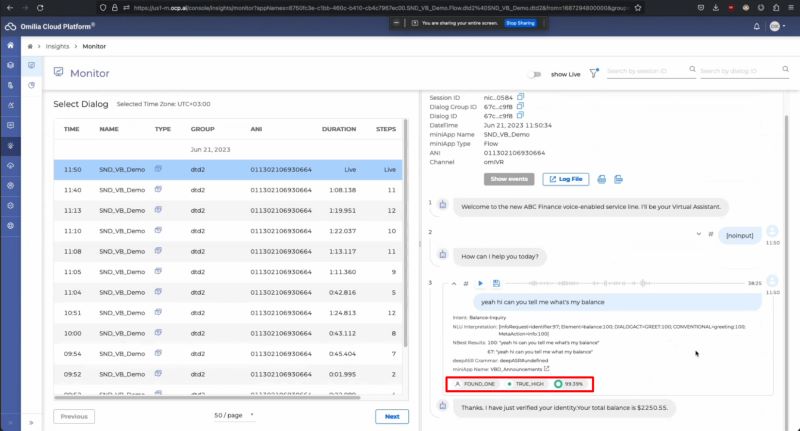
Verify customer identity through NICE CXone’s voice biometrics. (Source: Omilia Natural Language Solution’s Vimeo)
When a customer calls, the system shows the verification results, from “False High,” which indicates that the contact’s voiceprint doesn’t match the enrolled voiceprint, to “True High,” which means the contact’s voiceprint matches the enrolled voiceprint. If you’re interested in this platform, familiarize yourself with its features. Its monthly subscription starts at $71 per user.
Best Practices for Preventing Fraud
To further combat call center fraud, businesses must adopt specific security measures on top of maximizing fraud detection tools. Follow these best practices to keep bad actors at bay and reduce costly damages.
Fraudsters share similar moods and habits. In terms of sentiment, they’re often angry and demanding, creating fear to force you to give up sensitive information. They might threaten legal action, for instance, when you don’t let them change contact details without verification.
In terms of conduct, they have a hard time answering personal or security-related questions. They would also want to get special treatment or exceptions from security procedures. Agents must be aware of these scammer practices.
MFA requires users to provide proof of their identity from two or more authentication factors before they’re granted access. Authentication factors may be something the user knows, say, the answer to a security-related question, something they have, like a smartphone that receives a one-time passcode, or something they are, such as a voiceprint.
Even if a fraudster successfully stole login credentials from the dark web, they’ll have a hard time accessing accounts when there’s an MFA that adds a layer of call center security.
The risk of data breaches increases when too many individuals can freely retrieve data. As much as possible, reduce the number of people with access to confidential information. For those who need data, employ system permissions. When a team member leaves the organization, a proper offboarding process should include removing data access.
Encryption is the process of scrambling data into an unreadable format so that only authorized individuals can read it. At the very least, customers’ personal identifiable information, financial data, and voice recordings should be encrypted. Go for call center systems that offer data in-transit and data at-rest, protecting information being transferred between locations and those stored on servers and databases.
As mentioned, fraudsters often leverage fear to coax sensitive information. When there’s tension in the conversation, it’s easy to give in to requests and make exceptions to pacify the posing customer and resolve the issue faster. However, if accommodating requests means bypassing security procedures, you become more vulnerable to fraud. That said, it’s best to stick to the established security protocols and not make any exceptions for anybody.
Frequently Asked Questions (FAQs)
When you see the signs of call center scams, disconnect. Remember that fraudsters have mastered manipulation, so the longer you stay on the call, the greater the risk of falling victim to their schemes. Report the incident to managers and appropriate government agencies, describing the call with details so the authorities can keep an eye on scammers’ tactics.
No, your phone won’t be hacked by simply answering a phone call. However, scammers may use social engineering tactics to compel you to reveal confidential information to help them infiltrate your system or access records.
Call center phone systems programmatically ask callers to state their names before being connected to an agent. If the caller’s number matches a database record, the name automatically appears. In addition, you may verify a phone call through the voice biometric system, which facilitates identity authentication using voice analysis.
Bottom Line
Call center fraud happens when an individual contacts a call center and poses as a customer or a legitimate representative of a business entity to gain access to user accounts or information. Falling victim to scams can place businesses at serious financial risk and can result in loss of revenue, reputation, and customer trust and loyalty.
To prevent call center fraud, companies should use fraud detection tools, train agents to recognize scams quickly, and strengthen data security protocols. Consider the best call center systems as you improve business communications.