Every small business that processes credit card payments is required to be Payment Card Industry (PCI)-compliant. PCI compliance involves meeting the 12 requirements outlined by the Payment Card Industry Data Security Standard (PCI DSS), which is designed to ensure payment security and protect both merchants and cardholders from fraud.
- The PCI Security Standards Council is an independent panel commissioned by major credit card companies like Visa.
- Achieving PCI compliance for small businesses is done by completing and submitting a Self-assessment Questionnaire and Attestation of Compliance provided by the PCI Security Standards Council annually and completing internal and external vulnerability scans.
- Besides small businesses, merchants, service providers, payment processors, and payment gateways need to be PCI-compliant.
- Non-compliance can result in penalties, fines, fees, legal action, and damaged reputation in the case of a data breach.
Below is the list of the 12 PCI requirements categorized according to the six main goals that small businesses should follow to maintain PCI compliance:
Goal | PCI Requirements/Checklist |
|---|---|
Build and maintain a secure physical network |
|
Protect account data |
|
Maintain a vulnerability management program |
|
Implement strong access control measures |
|
Regularly monitor and test networks |
|
Maintain an information security policy |
|
Who Needs to Be PCI Compliant?
Anyone involved in processing payments—merchants, service providers, payment processors, and payment gateways—all need to adhere to PCI DSS guidelines. Cybersecurity is a top concern for many small and midsize businesses (SMBs), with 54% saying they are more concerned about it now than a year ago. In the 2023 Verizon Data Breach Investigation Report, small businesses (less than 1,000 employees) reported 699 incidents, while large businesses (more than 1,000 employees) reported 496 incidents.
While security standards are regularly evaluated and updated, the underlying goals for payment security stay the same. You will need firewalls for physical security, data security, upgraded technology (including a secure POS system), and the latest antivirus software. Compliance is expected to be an ongoing process for businesses and organizations, while validation is required on an annual basis.
How to Get PCI Compliance for Your Small Business
Here are the steps to PCI compliance broken down in detail:
Step 1: Determine Which PCI Compliance Level You Belong To
There are different levels of PCI compliance for businesses of different sizes, each with its own set of specific requirements and guidelines. Many times, your merchant service provider or payment processor will provide some level of PCI compliance, but there are still steps you must take as the merchant. First, determine which level is applicable to you.
Level 1 | Businesses processing 6 million+ annual Visa transactions |
Level 2 | Businesses processing 1 to 6 million annual Visa transactions |
Level 3 | Businesses processing 20,000 to 1 million annual Visa ecommerce transactions |
Level 4 | Businesses processing <20,000 annual Visa ecommerce transactions; businesses processing up to 1 million annual Visa transactions (non-ecommerce) |
Most small brick-and-mortar businesses will fall under Level 4 PCI compliance. Small online businesses will most likely belong to Level 3. However, note that merchants that experience a security breach that resulted in an account data compromise may be required to have a higher level of PCI compliance.
Did you know?
Based on the most recent Hiscox Cyber Readiness Report, 48% of companies reported a cyber-attack in 2022, up from 43% in 2021.
Step 2: Fill Out the PCI Compliance Self-assessment Questionnaire (SAQ)
All small to midsize merchants (Level 4) accepting major credit cards must complete an SAQ for part of the PCI compliance requirements. This form should be duly signed by a company officer and submitted to the acquiring bank once a year. You can access guidelines at the official PCI DSS website and determine which SAQ applies to you. For example:
- If you run an online business and use Shopify as your payment gateway and processor, you would fill out the SAQ-A.
- A brick-and-mortar business that uses a POS system and terminal, such as Lightspeed, would need to use the SAQ-C document.
- For manual entry with a virtual terminal, such as when you accept phone orders or invoices online, you are required to complete SAQ-C-VT.
This is just one of 16 pages you must fill out for the SAQ-A.
Tips for Filling Out an SAQ:
- The SAQ expects “yes or no” answers to the listed questions along with testing procedures relevant to each. Use these testing procedures as a method to verify your compliance and confidently answer the questionnaire.
- The last section of the SAQ allows you to specify your action plan should you fail any of the PCI DSS Requirements, which includes the steps you are taking and the estimated date by which you expect to complete these steps.
- If you are unsure of what to do, consider working with a qualified security assessor (QSA) firm to help with the self-assessment process.
Step 3: Investigate Your Payment Technology
While cloud users might be more susceptible (cyber-attacks on web applications grew 128% in 2022 compared to 2021), the advantages of running your business using the cloud far outweigh those risks, especially since there are steps you can take to safeguard data.
You’ll want to choose from the best PCI-compliant payment gateways, and if you run a storefront, you also need to secure your POS (point-of-sale) system from data breaches.
A Secure Sockets Layer (SSL) certificate alone does not make your website PCI-compliant. This bit of code that encrypts communication between your website and a web browser is most useful when selling and accepting payments online. However, it does not secure a web server from cyberattacks. You will need additional steps to satisfy PCI compliance to establish complete ecommerce payment security.
Tips for Investigating Your Payment Technology:
- When looking at the tools and systems you use to run your small business, look for the ability to create dedicated user accounts and logins. Only the people who need access should be able to acquire consumer data, and you should be able to track who sees what.
- Two-factor authentication and point-to-point encryption (P2PE) are other good security features, especially for cyber-attacks aimed at stealing customer credentials.
- Install all your vendor’s security patches and updates in a timely manner. Otherwise, you run the risk of vulnerability. Remember to check your settings, too. Nearly half of businesses never change their vendor’s default settings.
Step 4: Create & Document Security & Compliance Processes
Interestingly, a recent UpCity study found that while 80% of small business owners have been increasingly aware of the dangers of cyber theft, 50% of SMBs still have no cybersecurity plan in place. You might not have a full-fledged data privacy team to help with security, but whoever is responsible for ensuring PCI compliance should also create processes for the rest of the business to follow.
It’s important to communicate your new PCI compliance measures, why they are important, and how the rest of your staff can contribute. This became even more significant during the pandemic. Around 51% of businesses worldwide say that they have experienced more targeted cyber attacks with remote work setups.
Tips for Establishing Your Security and Compliance Process:
- Maintain a policy to ensure staff understands the importance of PCI compliance and what to do and not do with consumer data. (For example, staff should enter customer payment information directly into the processor instead of writing it down.)
- Create a security policy and governance plan to map out how you’ll continue to maintain compliance. Remember to check for physical tampering with POS systems and card readers as part of your data security governance—it’s not all limited to software solutions. Learn more tips on how to properly secure your POS system.
- The PCI Security Standards website includes PCI awareness training, which may help in complying with PCI DSS Requirement 12 to provide general security awareness education for employees.
Step 5: Complete Your Attestation of Compliance (AoC)
The AoC is a document you’ll use if you’re self-auditing or a QSA will use to declare your business’ level of compliance. The form should be completed, signed, and submitted along with the SAQ and the approved scanning vendor (ASV) results, which we discuss below. Businesses are expected to submit an AoC annually.
The SAQ review may be completed in person or virtually, depending on your QSA’s preferences. If they determine from your SAQ that you are PCI-compliant, you will receive your AoC from them.
When a merchant uses a third-party payment processor, most of these PCI compliance requirements are met. However, you still need to be aware of the regulations, and you must meet environmental PCI compliance, such as with firewalls, strong passwords, and restricting access to cardholder data.
Step 6: Prove PCI Compliance With a Vulnerability Scan
If your small business accepts credit cards, you may have to pay for regular vulnerability scans with an Approved Scan Vendor (ASV), which is a third-party company that will conduct quarterly vulnerability scans to validate your PCI compliance. The ASV will determine whether you’re doing everything possible to safeguard consumer credit card and contact information.
What Is a Vulnerability Scan?
An external vulnerability scan is performed by an ASV to determine whether your network is secure and safe for consumers. An ASV can also perform internal scans to detect vulnerabilities, but many merchants choose to do it themselves with the appropriate SAQ.
The external scan looks for vulnerabilities in your network firewalls, while an internal one looks for holes in your business’ firewalls. Both are necessary, but the internal scan can be self-performed.
An ASV will give you either a pass or fail each quarter, which you’ll need to submit to the PCI DSS council. If you make any changes to your network, you’ll have to schedule a new scan, as failure can occur when minor changes take place. For example, your internet service provider (ISP) may change your public-facing IP number, and your ASV might be scanning your old one, which could result in “host not detected.”
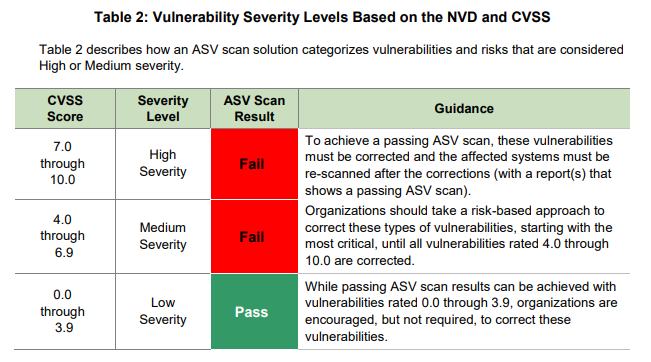
All internet-facing system components that are part of and provide access to the cardholder data environment (CDE) will be evaluated according to severity levels. (Source: PCI Data Security Standards)
Tips for Choosing an Approved Scanning Vendor:
- Choose from PCI Security Standard Council’s Approved Scanning Vendors list.
- Make sure that your chosen vendor has enough experience working with businesses that are similar to yours.
- Look for vendors with the latest scanning engine technology that (1) can run during your business hours without compromising the network and (2) has measures in place to minimize “false-positives” results.
- Consider vendors that offer unlimited scanning and rescanning, as vulnerability scans, while only required quarterly, are encouraged to be done on a more regular basis.
Step 7: Submit PCI Compliance Documentation
Gather all your documents and submit your PCI DSS report to the PCI DSS council either through an e-file option or through snail mail.
The report will include:
- Summary of Findings: Composed of a general statement and details of the security assessment
- Audit Details: This will list all the testing procedures and implementation questions for all your relevant business framework specifications organized per Requirement
- Business Information: This is a summary of your business profile as indicated in your SAQ
- Card Payment Infrastructure: Documents such as your network diagram, transaction flow diagram, details of your wireless LAN setups, list of POS products being used including wireless POS terminals
- Details of External Relationships: This is a list of service providers that share your cardholder data, including card payment companies and other business entities that require compliance with PCI DSS
Step 8: Track & Test Your Systems
Data security and PCI compliance aren’t set-it-and-forget-it. It’s important to test your security measures often to ensure they’re working as intended. Only a little more than half of organizations successfully test their data security programs, and only two-thirds track and monitor system access adequately. The 12-point requirement details how you can maintain PCI compliance between assessment periods.
Tips for Maintaining PCI Compliance:
- Periodically: Keep all your antivirus software, intrusion detection, and prevention engines up-to-date and performing regular scans.
- Daily: Use log harvesting, parsing, and alerting tools to record security events. Adopt a reputable source for security vulnerability information and establish a process for identifying and assigning risk rankings.
- Weekly: Install a change-detection software to monitor and identify modifications to critical files.
- Monthly: Install vendor-supplied critical and non-critical security patches within one month of release.
- Quarterly: Perform system scanning through AVS.
- Semi-annually: Perform and document reviews to ensure that your firewall and router configurations meet PCI compliance standards
- Annually: Conduct system audits, security testing, and risk assessment procedures. Review your information security policies and public-facing web apps. Hold security awareness training for your employees.
Why Is PCI Compliance Important for Small Businesses?
Builds Consumer Confidence
Not only is every business susceptible to data breaches, but consumers are increasingly aware of the steps merchants can take to protect their information. And this is influencing their purchase decisions.
One survey in 2022 found that 89% of consumers care about data privacy, and 44% say they have switched companies because of company data policies and practices.
Protect Against Data Breach
Reports of data breaches in large companies like Capital One in 2019 and Microsoft in 2021 have left consumers wary about sharing their financial information, more so with smaller businesses. Many companies, particularly SMBs, have serious challenges when it comes to data security. A 2020 edition of Verizon’s Payment Security Report illustrates this impact:
Plus, many businesses aren’t even sure if they’re maintaining PCI compliance. A cybercriminal can exploit known vulnerabilities in websites, firewalls, and insecure remote access to acquire valuable credit card data. Consider another infamous data breach, this time suffered by Equifax in 2017, when more than 182,000 credit card numbers were exposed. That sort of breach is damaging for credit card companies, banks, and small merchants.
Did you know?
According to the Verizon 2022 Payment Security Report, PCI compliance increased in 2020—the first time since 2016. Around 43.4% of organizations are PCI-compliant in 2020, which is a huge jump from 2019’s 27.9%.
Be Prepared in Case of Data Breach
In 2022, the average cost of a data breach is $4.35 million, an increase of 12.7% from 2020. In the same study, around 83% of organizations have experienced more than one data breach.
Should you face a data breach, you might also ruin customer trust. Some three-fourths of online shoppers are more likely to buy from large retailers, according to a 2023 BrizFeel survey, because consumers believe the bigger businesses take security seriously. Consumers are very much aware of security issues and data breaches, with 43% of consumers saying they don’t trust companies to follow stated data policies.
Being PCI-compliant means you have an up-to-date incident response plan in place outlined in PCI DSS Requirement 12. The entire guideline can also serve as a sound starting point for effective emergency response management and forensic investigation processes to help mitigate the cost in the event of cyberattacks that result in data breach.
How Much Does PCI Compliance Cost?
To ensure your business maintains PCI compliance, you may be subject to various fees. These could be monthly or annual fees, and their costs range from $10 per month to hundreds of dollars per year. It depends on the service, the type of payment processor you choose, and how you plan to handle AoC and vulnerability scans.
Typically, payment processors like Square and Shopify won’t charge a separate fee for PCI compliance. Rather, they roll the cost of compliance into your monthly or transaction fees. A traditional merchant account may come with an added compliance fee, or it’s rolled into a statement fee. Chase Merchant Services, for example, doesn’t charge anything for PCI compliance in its pay-as-you-go plan.
Where you can expect to pay PCI compliance fees are when you need a vulnerability scan or you want to hire a QSA:
- ASV scans: Quarterly vulnerability scans of your business environment, such as for firewalls, internet, and so on, are typically charged annually; the average range is from $200 to $1,000.
- QSA service: Merchants with multiple locations might want to hire a QSA for PCI compliance; the fees start at $10,000 and vary based on the number of locations and complexity of networks.
Charging fees for PCI compliance is common, as these fees go toward keeping data servers updated and maintained and all data security firmly in place. Your payment processor, payment gateway, or service provider is in charge of data transmission and storage, so it’s an important and necessary fee however it’s charged.
PCI compliance is a set of standards, not actual laws, so it’s regulated by the credit card companies. So, what’s the worst-case scenario if you remain noncompliant? Here are some possibilities:
- PCI noncompliance fee: You’ll pay $19.95 (or more) per month until you prove your business is PCI-compliant (although it appears to come from your payment processor, it’s from the credit card companies, but some processors may charge more).
- PCI noncompliance fine: A security breach occurs, and consumer data is leaked; your records show noncompliance; you’ll pay $5,000 to $100,000 per month of noncompliance.
- PCI noncompliance and revocation: Your acquiring bank revokes your ability to accept credit cards, which could be the end of your business.
What Do I Need for PCI DSS v4.0?
In March 2022, the PCI Security Standards Council published the PCI Data Security Standards v4.0. Updates to the requirements were focused on ensuring that businesses have security measures in place that can match a more dynamic and fast-evolving technology in the payment industry.
During the two-year transition period, both v3.2.1 and v4.0 are applicable—businesses and organizations are not required to meet the full PCI DSS v4.0 requirements, but they are encouraged to do so to prepare for the full implementation.
By March 31, 2024, PCI DSS v3.2.1 will be retired, and v4.0 will be the only active version. If you are up for your annual PCI compliance validation, it is recommended to follow the v4.0 requirements to ensure your compliance upon its full implementation.
The new version features 64 new requirements, but only 13 of those are required by April 1, 2024. The rest will only be required for compliance by March 31, 2025.
Here are some tips on how to prepare your business for PCI DSS v4.0
- Start now: Do not delay any preparations for meeting the new requirements for PCI DSS v4.0. Full implementation is inevitable so it is best to start early.
- Start strong: If you are compliant with PCI DSS v3.2.1, make sure you are taking the proper measures to stay compliant. All the requirements for v3.2.1 are still included in v4.0–nothing is removed so having strong compliance with v3.2.1 is a good start. If you are not yet compliant with v3.2.1, then it is a must to work toward that as soon as possible.
- Understand the new requirements: From now until March 31, 2024, you will need to meet 13 requirements in addition to the ones for PCI DSS v3.2.1. Download the full documentation of the summary of changes from PCI DSS v3.2.1 to v4.0:
PCI Compliance Frequently Asked Questions (FAQ)
Yes. Small businesses are more susceptible to data breach. A Level 4 PCI compliance is required for small businesses, which includes a minimum quarterly scan and annual submission of a Self-assessment Questionnaire (SAQ).
Small businesses that process less than $20,000 in transactions per year are required to submit a Self-assessment Questionnaire (SAQ) and an Attestation of Compliance (AoC) once a year. You will also need to establish, document, and maintain a security policy for your company.
For small businesses, third-party security professionals would charge around $50–$200 for the Self-assessment Questionnaire (SAQ). The cost for vulnerability scanning starts at $100 per IP address; remediation work also starts at $100, but can increase quickly depending on what needs to be done (software updates, hardware replacements, etc). Security awareness training can cost around $50–$70 per employee.
It’s advisable to consult with security professionals to ensure that you are accurately performing the necessary steps, but you can minimize the cost by choosing the right merchant service provider. After that, you may start filling out the SAQ and maintain security scan records on your own.
Bottom Line
It is ever more critical for merchants to take PCI compliance for their small businesses seriously. Don’t assume that just because your payment processor is compliant, you’re off the hook. Follow the guidelines and be sure to check the official website for any changes. The PCI compliance requirements evolve as data security does.