Bring your own device, or BYOD, refers to a type of company policy that allows employees to use their own personal devices (e.g., laptops and smartphones) to work on business-related tasks, instead of company-issued equipment. In a survey cited in the 2022 Global Mobile Threat report, 66% of companies had an active BYOD program in place, while an additional 11% were considering rolling out the policy in 2023.
For most organizations, BYOD makes sense for reducing overhead costs and offering employees flexibility in choosing devices for work. This article further explores what a bring your own device policy is, how it works, and when it’s ideal to adopt such a system.
How the Bring Your Own Device Policy Works
The best way to answer the frequently asked question, “What is a bring your own device policy?” is to understand how it works. Essentially, the implementation of the guidelines involves three stages: writing the policy, registering employees’ devices, and training team members to ensure data security.
Drafting the Policy
A written bring your own device policy outlines the rules for proper usage, security measures, and employer support. These elements below should be part of your document:
- Eligibility: State which employees and devices qualify for the program. Most organizations qualify team members based on their role, mobile usage, and business travel frequency. In terms of the devices, specify the types of devices and operating systems your information technology (IT) team will have support for.
- Acceptable use: Define clearly which activities an employee can perform on their devices while connected to the corporate network. List the apps that can and cannot be downloaded. Identify the company-owned resources that can be accessed through mobile devices, e.g., emails, calendars, and documents.
- Security: Outline the security measures employees must follow to protect confidential company data. These should include using strong passwords, locking the device with a PIN, and enabling automatic lock after a specific number of failed login attempts. State in the policy that you’ll enforce remote wiping of data for specific situations, such as when the device gets lost or when the IT team detects a breach.
- Legal issues: Take into account the legal consequences of your bring your own device policy, including data ownership, privacy expectations, and device confiscation.
- Change and support: Establish protocols for changes in the company, for example, when an employee leaves the organization, a device gets damaged or stolen, or a lost device gets recovered. It must be clear in bring your own device policies which support channels are available to report these incidents.
Get started on drafting your BYOD policy by downloading our BYOD agreement template. Customize and improve it according to your specific business needs.
Onboarding Devices
After drafting the actual policy and releasing it for everyone’s information, roll out the registration of devices. Make the enrollment process easier for employees by setting up a registration platform and providing step-by-step instructions for enrolling devices. For this, you have the option to develop your own registration platform or use mobile device management (MDM) software.
The latter is best for companies wanting to deploy device registration faster. An MDM solution catalogs all the devices connected to the company’s network, providing them access to company data and email, secure VPN, and password-protected apps. With its location tracking capability, it alerts administrators about high-risk and non-compliant devices and remotely locks or wipes data from lost or stolen devices.
Training for BYOD Compliance
After the registration of devices, communicate to employees the importance of following security measures to avoid compromising confidential data. Some written BYOD policies are long, with some having legal jargon, that team members will sign without understanding its requirements and implications. Thus, it’s important to have a sit-down discussion where each of the points mentioned in the policy is talked about, and employees are free to ask questions.
History of Bring Your Own Device Policies
Now that you know what a bring your own device policy is, let’s take a look at how it was first developed. The term BYOD was first used by voice-over-internet-protocol (VoIP) solution BroadVoice in 2004 when the company let clients bring their own devices for their calling plans.
However, it was only in 2010 that the BYOD policy hit the mainstream. During this time, Android was rising in popularity, and the first iPad by Apple was released. Many employees use their smartphones and tablets in the workplace. Initially, companies prevented personal devices from connecting to the corporate network.
However, mobile devices continued to be more popular, as they offered convenience of access. Eventually, organizations realized that the only way to adapt to this emerging trend is to adopt BYOD. The first official BYOD policies were released in 2011.
Advantages of Bring Your Own Device Policy
Given the rise in remote work and the steady increase in smartphone ownership, many companies are looking to adopt a BYOD policy to support employees. The emphasis on team collaboration pushes organizations to allow personal devices for work-related activities and to make communication with colleagues easier. Here are the specific benefits of a BYOD policy for small businesses:
With a BYOD policy, there’s no need to buy new phones and laptops for every employee. The savings don’t stop with the upfront cost, as you’ll also slash expenses in terms of replacements. Most employees tend to be more careful when using their own devices versus company-issued technologies. However, note that you may need to cover employees’ cell phone data plans when you adopt a BYOD policy.
Since employees use their own devices, they’re already familiar with navigating the system and using the different apps. There’s no learning curve, and they are able to immediately start working on tasks: replying to emails, attending virtual meetings, and collaborating with team members via instant messaging.
Many small business VoIP solutions supporting BYOD have easy-to-navigate interfaces, which make it easier to connect with customers and colleagues. Some are equipped with team chat and video conferencing tools, allowing users to collaborate with each other without needing to use personal messaging apps.
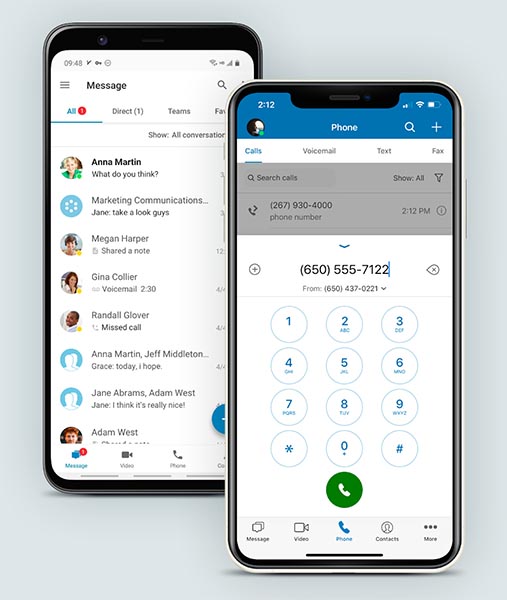
RingCentral supports BYOD and features advanced calling and team chat.
(Source: RingCentral)
RingCentral, a popular VoIP provider, enables businesses to bring their own devices when using its platform. Desk phones can be configured with assisted or manual provisioning, with the step-by-step process detailed on the provider’s website.
Since the provider is a cloud-based unified communications platform, smartphones and tablets also have access to voice calling, instant messaging, and video meeting features. This reduces the need for external apps used for personal communications. Its monthly subscription starts at $30 per user. Learn more about the provider in our comprehensive RingCentral review.
Some employees like Android operating systems, while others favor iOS. Some prefer Windows over Mac and vice versa. By giving team members the freedom to use the devices they want, they not only become productive in their work but also get a morale boost.
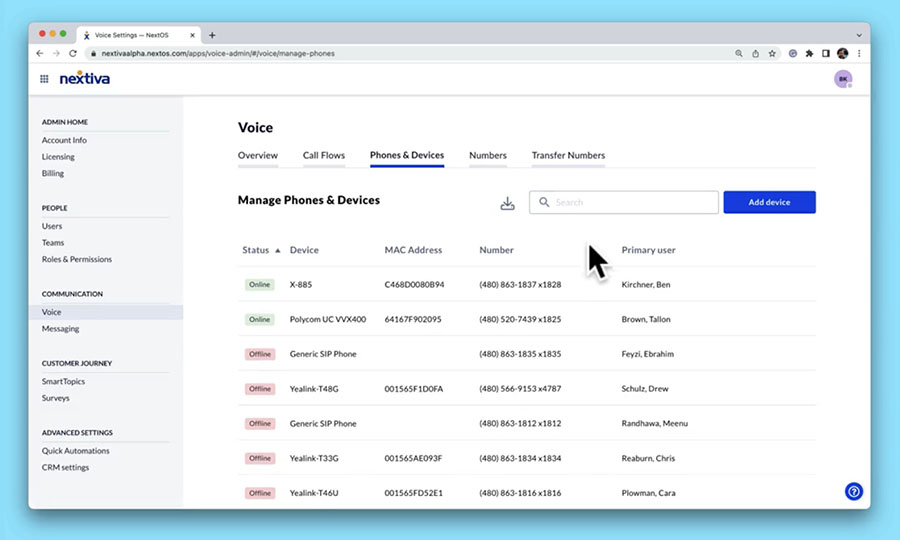
Manage multiple phones easily on NextivaOS. (Source: Nextiva)
Reliable VoIP provider Nextiva also supports BYOD and makes tracking multiple phones easier with its device management feature. It lists all the connected devices along with their respective phone numbers, users, and statuses. BYOD support is available in all of Nextiva’s subscription plans, which start at a monthly price of $30.95 per user. If you want to learn more about the provider’s features and pricing, refer to our Nextiva review.
Employees tend to keep their own software systems updated. They are also more likely to upgrade to newer devices whenever a new smartphone or laptop comes out in the market. With a BYOD policy, your business can take advantage of the latest technologies without the hefty overhead costs.
Disadvantages of Bring Your Own Device Policy
While BYOD offers many benefits to businesses, it’s not for everyone, especially in the case of companies with employees refusing to use their own devices for work. Team members hesitate to use their own devices for work for various reasons, including the blurred lines between personal and business data.
Below are some more disadvantages associated with BYOD policies:
Although a BYOD policy accommodates employee preferences, it creates complications for the management. A diverse set of devices may present compatibility issues with your company’s proprietary apps. The same software may have different versions for various operating systems as well, which may make collaboration difficult among team members.
Personal devices carry different sources of distraction, from social media to video streaming services and game apps. With only a few taps on the screen, they’ll be pulled in and easily get sidetracked from work.
To minimize distractions, some bring your own device policy templates include blocking access to particular websites during business hours or when employees are connected to the company’s network. When you draft your own, make sure that the policy is clear on which websites are restricted.
Employees typically bring personal devices wherever they go, not only when they go home from work, but also when running errands or attending social events. This puts devices (along with your company data) at risk for theft or misplacement.
Moreover, employees who aren’t careful may unintentionally share confidential information through unsecured public Wi-Fi. As you write your company regulations, refer to bring your own device policy examples to get ideas on how to beef up data security measures.
Bring Your Own Device Best Practices
If BYOD is the ideal enterprise mobility setup for your company, adopt routines that will address employees’ privacy concerns and protect the integrity of company information. When you get the full support and cooperation of employees on upholding security measures, BYOD will be a cost-efficient, productivity-boosting setup for the business.
As you consider BYOD policy examples, ask your IT and legal departments for the best practices to adopt. Below are some you may consider imparting to your workforce:
To give employees peace of mind about your BYOD program, spell out in the policy how personal and company data will be kept separate. For example, use a mobile device management (MDM) solution to create a “workspace” within the device and segregate personal and work apps. With this, when an employee downloads an app, it will be added to their personal apps, which won’t be accessed by the company. At the same time, the personal apps won’t have access to business data.
Security risks go beyond connecting to an unsecured Wi-Fi network and losing a mobile device. Personal laptops and smartphones are at risk of getting infected with malware, which increases the risk of data leaks. Moreover, some employees may be vulnerable to phishing and other cyberattacks. Given this, enforce strict security measures, including the ones mentioned below and typically included in BYOD policy templates:
- Use a strong password, with clear parameters for length, special characters, and capital letters.
- Prompt two-factor authentication in accessing company apps.
- Enable automatic device lock when the smartphone or laptop has been idle for a certain period or after a specific number of failed login attempts.
- Install anti-malware software on your employees’ personal devices.
- Prevent app downloads from suspicious websites.
- Execute remote wipe for lost or stolen devices.
- Encrypt business communications, especially those sent through company apps.
Define the consequences of policy violations and make sure that employees understand them well during training. The penalties may range from a verbal or written warning to removal of system access to employment termination. Emphasize that stern penalties are critical in enforcing strict security measures.
An important part of the written BYOD policy and training is including a clear plan for employees who leave the company. Communicating this as early as the onboarding process will prevent costly misunderstandings later and ensure that you still have full control over company data in the event of a team member’s resignation, termination, or layoff.
Make sure that all employees understand the specific steps involved in the offboarding plan, including enforcing remote wipe and revoking network access.
Automate device enrollment and configuration to reduce manual work on the part of the employees and the IT team. If possible, automate the app vetting process as well to ensure that software solutions don’t contain malware.
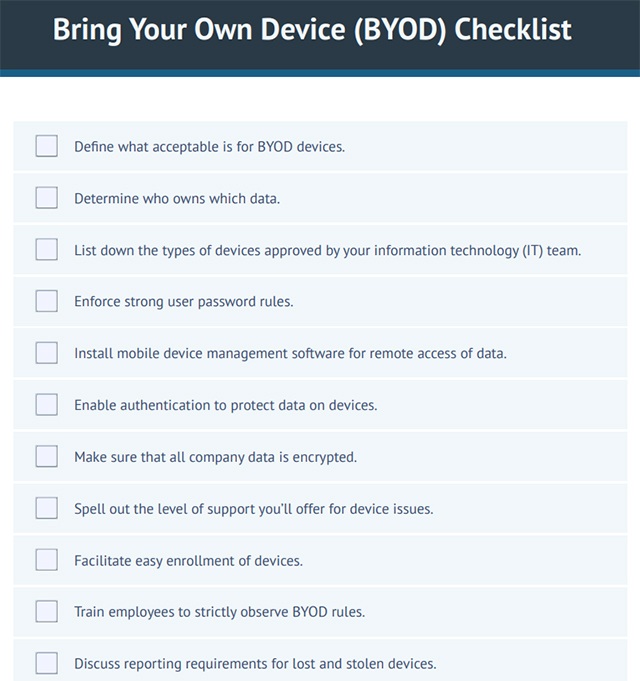
To help you remember these best practices when rolling out BYOD policies, we put together a BYOD checklist. Use it as a reference for drafting and polishing your guidelines.
Frequently Asked Questions (FAQs)
The three levels of BYOD refer to the degree of an employee’s access to company assets. These include:
- Level 1: Basic access, where employees are able to use email and calendar on their personal devices, but not corporate resources.
- Level 2: Controlled access, where employees are able to use corporate resources, such as data and applications, with a high level of security.
- Level 3: Full access, where employees are able to use all corporate resources with minimal security measures.
If you think BYOD isn’t the ideal enterprise mobility strategy for your business, there are many more alternative solutions, such as:
- COPE (Company Owned/Personally Enabled): Employees get a pre-approved device that abides by the company’s MDM solution. While primarily for work, the device can be used for personal activities.
- CYOD (Choose Your Own Device): Employees are allowed to choose among devices the company offers. The organization manages the devices but permits personal use.
- COBO (Company Owned/Business Only): Employees get a pre-approved device, and the company strictly dedicates it to work, prohibiting personal use.
The end users or employees pay for the expenses associated with owning personal devices, but some companies offer reimbursements for the cell data plan or lost or stolen devices. Some states, like California, require employers to reimburse workers for any business-required use of personal phones. In this case, a clear reimbursement policy should be part of your BYOD program.
Bottom Line
A BYOD policy benefits businesses in various ways: cost savings, a faster transition to enterprise mobility, and improved employee morale over the freedom to use their own devices. However, it also comes with a host of security risks and a broad range of IT responsibilities.
If you’re set on adopting a BYOD policy, write clearly defined guidelines for preventing data leakage, educate the workforce properly, and invest in a well-equipped and properly trained IT team. As you refer to more examples of BYOD policies online, consider communication software providers that support bringing personal devices, such as RingCentral. Sign up for its 14-day free trial today.