Voice-over-internet-protocol (VoIP) tools offer rich features and support mobility, but they come with serious risks that cause damage to a company’s reputation and operations. Cybercriminals hack phone systems to listen to calls, steal confidential information, and extort money in exchange for not leaking data. To avoid falling victim to these cyberattacks, beware of VoIP security threats and ensure your business phone systems are protected.
In this article, we’ll explore various security vulnerabilities and the ways to protect your organization.
1. DDoS (Distributed Denial of Service) Attacks
A distributed denial-of-service (DDoS) is among the most popular types of VoIP security threats, interrupting a target server’s normal traffic by overwhelming the system with multiple calls. A server uses computational power and memory to authenticate call requests. With so many calls flooding the system, the server cannot process legitimate calls. These are the signs your VoIP platform is under a DDoS attack:
- A huge amount of traffic coming from a single IP address
- A sudden traffic increase at unusual hours of the day
- Delayed or failed calls and messages
How to Protect Your Business
Prevent DDoS attacks by using encryption and a virtual private network (VPN). Engage with multiple independent internet service providers to separate connections for VoIP and general systems. Should the attack happen, the damage won’t be as severe as having all your assets down. In addition, choose a business phone system with session border controllers that block DDoS attacks.
2. Vishing
Vishing is voice phishing, a VoIP security risk where attackers use persuasive language to lure victims into sharing confidential information. Most criminals employ caller ID spoofing posing as an authority figure, a member of the police department, a bank, or a high-ranking official in the company, instructing an employee to send confidential documents. Unsuspecting employees fall for the trap, unintentionally leaking sensitive data that could be used for extortion later.
A usual sign of vishing is a frantic sense of urgency. They will use threats of arrest and warrants or talk about account problems that need to be addressed right away to make you reveal certain information.
How to Protect Your Business
To avoid this type of security threat, train your workforce in discerning vishing attempts. They should have their guard up when a caller asks for personally identifiable information or login credentials. Additionally, they must report such suspicious calls so your cybersecurity team can review and improve data protection measures.
Use multi-factor authentication in your business phone system to ensure only authorized individuals can access confidential data in your organization. To further strengthen your system security, integrate your business phone with single sign-on (SSO) providers.
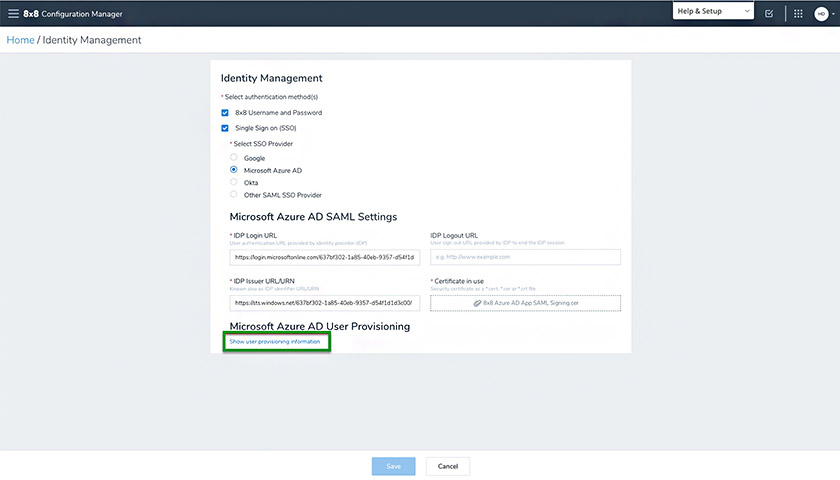
8×8 integrates with single sign-on provider Microsoft Azure. (Source: 8×8)
8×8 is a cloud-based business phone system that works seamlessly with SSO solutions, such as Okta and Azure. SSO reduces the number of cyberattacks as users are compelled to use one single, strong password. These tools also allow information technology teams to monitor the applications users access.
3. Packet Sniffing Attacks
This security risk involves intercepting sensitive data passing through a network in the form of packets. The most common packet sniffing attack is Transmission Control Protocol (TCP) session hijacking, wherein the hacker takes over a web user’s session ID as if they are the authorized user.
Once they have the user’s session ID, they’ll be able to do what the legitimate user is allowed to do in the system. This includes having access to confidential customer information. If you notice odd traffic in your network, like phone calls you don’t recognize, your network may have been compromised.
How to Protect Your Business
To avoid VoIP security threats from packet sniffing, use a VPN to encrypt your traffic and conceal your IP. Most phone systems have built-in threat detection and mitigation tools, which help businesses proactively address vulnerabilities and reduce data leak risks.
4. Malware & Virus Threats
Since VoIP mainly uses the internet, it’s vulnerable to malware and virus attacks. These VoIP security risks clog up network bandwidth, resulting in signal breakdowns. In addition, they render data unusable and inaccessible to users. They may also create backdoor entries, which make it easy for hackers to access your system and obtain confidential information.
The most common sign of a compromised system is website redirects. While placing and receiving customer calls, you might need to look up some information on the internet. If you get redirected to a different site every time you search or click a link from the results page, your VoIP system may have malware.
How to Protect Your Business
To avoid these VoIP threats, implement data security measures, such as encryption-at-rest and in-transit. Aside from encryption, use an Intrusion Detection System (IDS) to identify network infections. Consider adding a firewall that blocks malware and prevents access to suspicious websites.
Dialpad Meetings are encrypted, ensuring that information is only available to attendees. (Source: Dialpad)
Business phone systems like Dialpad offer enterprise-level encryption: Transport Layer Security (TLS) and Advanced Encryption Standard (AES) 256. The screen-sharing feature in Dialpad Meetings is encrypted from when the session starts until it ends, making information available only to meeting participants. Learn more about the capabilities of this VoIP provider by reading our Dialpad review.
5. Phreaking
Phreaking came from the words phone and freak. It’s one of the common VoIP attacks involving hacking into telecommunication systems and entering a PIN number to make free phone calls. It uses a device called a blue box, which mimics a telephone operator’s console and allows hackers to place calls bypassing the phone company switches.
Often, phreaking involves call forwarding to premium rate numbers, which cybercriminals own, generating profit in the process. Thus, excessive call charges are a common sign your system has been compromised.
How to Protect Your Business
To prevent phreaking attacks, encourage employees to change passwords and PINs and ensure that credentials aren’t predictable. When a team member resigns from your company, part of the offboarding process should be removing the user’s login details.
Aside from proper workforce training and offboarding, your business phone must also have stringent measures for international calls. In some virtual phone systems, international and offshore calling are disabled by default to avoid fraudulent and unauthorized calls.
6. Spam Over IP Technology (SPIT)
Spam Over IP Technology (SPIT) refers to unsolicited, auto-dialed VoIP telephone calls. Since VoIP calling is cheap, many telemarketers and pranksters take advantage of the technology to cause a disturbance, redirecting calls to a different country, thereby increasing the company’s operational costs.
Aside from costing you money, SPIT affects productivity. It takes agents’ precious time from important customer calls while clogging up voicemail boxes and making it harder to know which messages to prioritize.
How to Protect Your Business
Protect your business from these VoIP vulnerabilities by choosing a platform with robocall detection and blocking capabilities. This feature automatically alerts you when a spam call comes through, with a warning on the incoming call screen. Add the spam callers’ phone numbers to your blacklist so future calls will go straight to voicemail.
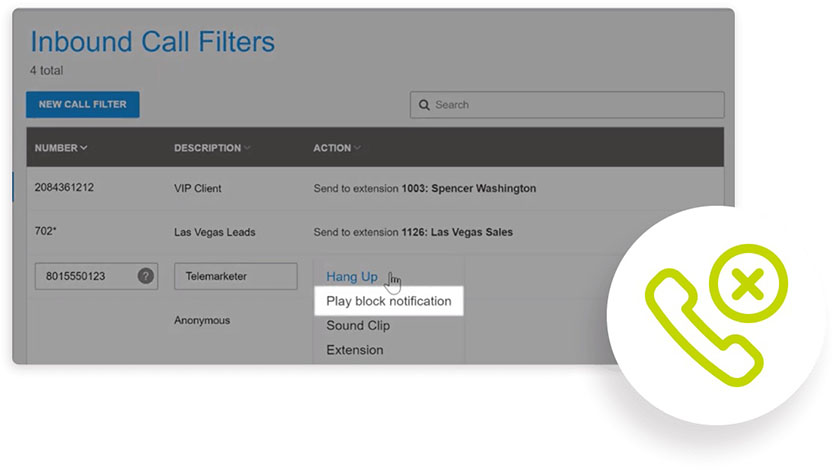
Use GoTo Connect’s inbound call filters to reject spam calls. (Source: GoTo Connect)
GoTo Connect is a reliable VoIP provider for reducing SPIT risks, as it features auto-reject call filters for spam calls. Depending on your settings, the suspicious call will be terminated as soon as it enters the phone system, or a short blacklisted message will be announced before the call ends. To learn more about this VoIP provider, check out our GoTo Connect review.
7. War Dialing
This security risk involves dialing several telephone numbers to find the ones connected to a computer modem. The process starts with hackers identifying a range of phone numbers, typically within a given prefix, like 456. They configure the war dialer software to dial all the phone numbers from 456-0000 to 456-9999 and save those connected to a modem.
Once they identify the target numbers, the hacker tries to access the computer modem through a vulnerable telephone line. After guessing the password, they’ll be able to access the system. The most obvious sign that you’re under a war dialing attack is when you hear phones ringing all over your office during off hours, and you get modem tones upon picking up the call.
How to Protect Your Business
To prevent unauthorized access from war dialing efforts, conduct penetration testing yourself, taking note of unsecured modems in your office. Avoid disruption of normal operations by doing this during off hours.
Additionally, review your hardware inventory and look at the computers connected to modems. Remove modems that are not in use and disable those embedded in the motherboard. For active modems, ensure that they require usernames and passwords.
8. VOMIT (Voice Over Misconfigured Internet Telephone)
VOMIT involves converting a phone call into a file that can be shared anywhere. Hackers often sell this data to competitors or use it to blackmail companies. In the same way, they are able to eavesdrop on ongoing calls, obtaining access to confidential information, such as usernames and passwords, call origin, and financial details.
How to Protect Your Business
A complete encryption solution is the best way to reduce security risks from VOMIT. It ensures that data is safe at every stage of its journey, including during transmission. If a breach happens, the raw data is useless to cybercriminals since it’s difficult to decode.
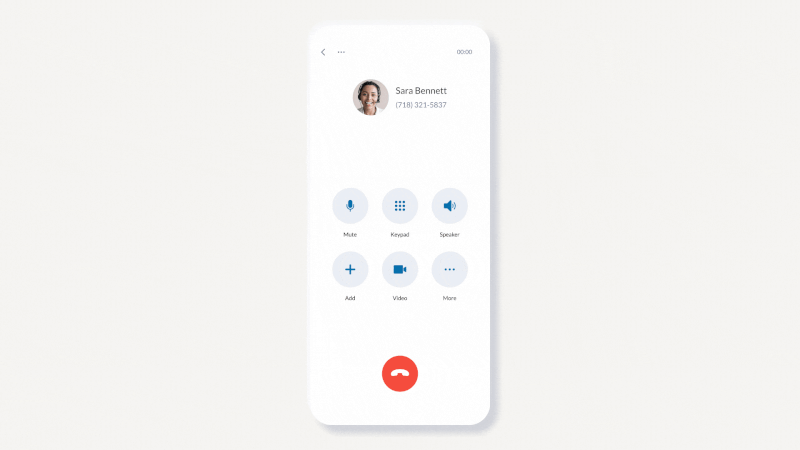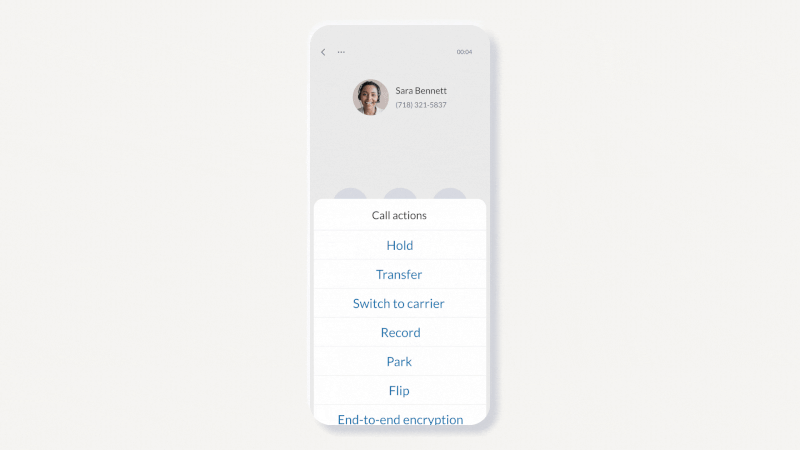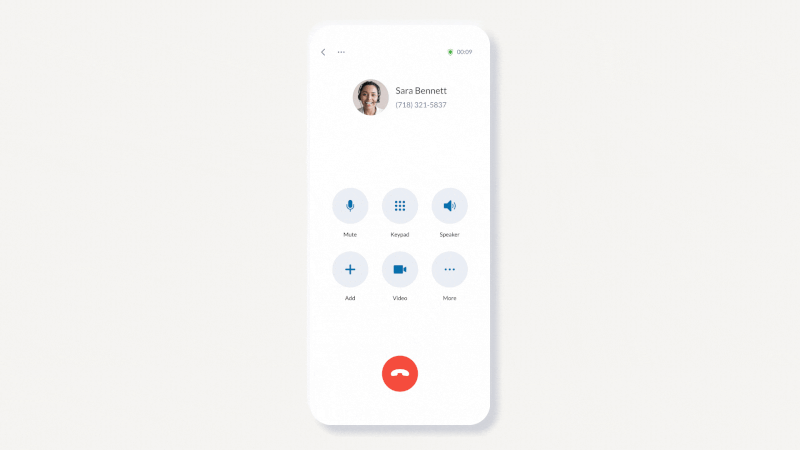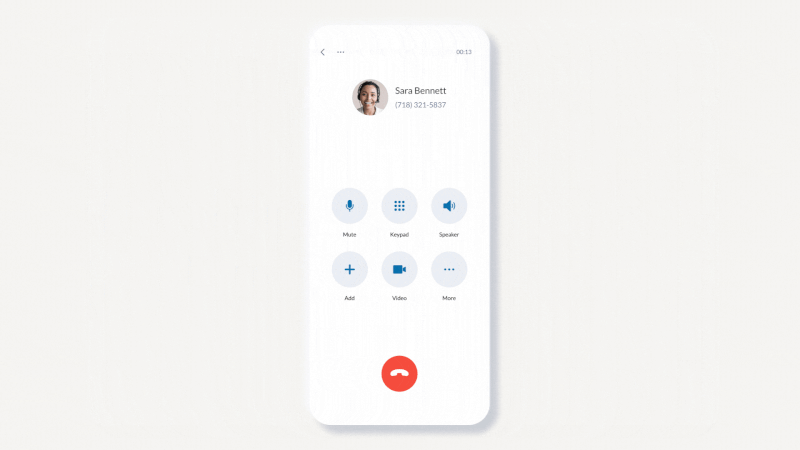
RingCentral enables users to set end-to-end encryption on calls. (Source: RingCentral)
RingCentral, our top pick for small business VoIP services, offers TLS and Secure Real-Time Transport Protocol (SRTP) encryption between all endpoints to ensure that communications within the platform are secure and safe. This applies to phone calls, messages, team chats, and video meetings. With this, you’ll have peace of mind that no one is able to eavesdrop on your most critical discussions with employees and customers.
9. Call Tampering
Call tampering is a VoIP attack that disrupts live calls by injecting additional noise packets into the call stream. Hackers may also delay the delivery of packets, and, as a result, call participants will experience a choppy connection or hear nothing for long periods. In the end, the participants hang up in frustration. If this keeps happening in your sales and customer service operations, leads and clients will most likely avoid calls from your business.
How to Protect Your Business
To avoid cyberattacks interrupting business calls, make sure that your phone system has strong authentication and encryption measures. Incoming and outgoing calls must be encrypted, and your IP phones must have authentication codes during off-hours.
10. Man-in-the-Middle (MiTM) Attack
The MiTM attack is a security threat wherein a hacker intercepts a conversation between two parties and disguises themselves as a legitimate service to let customers and employees enter confidential data.
The most common type of attack is domain name system (DNS) hijacking, which involves forging DNS records and sending users to fake websites, thus capturing login credentials and financial details. Aside from stealing information, MiTM attackers often install malware.
How to Protect Your Business
Aside from business phone encryption, ensuring that your organization only visits HTTPS websites will protect you from this security threat. Remind your remote team members to avoid open or public Wi-Fi networks, even those that look legitimate, because they might actually be fake networks set up to catch unsuspecting users. Another security measure worth considering is limiting access to specific data in your work apps and phone systems.
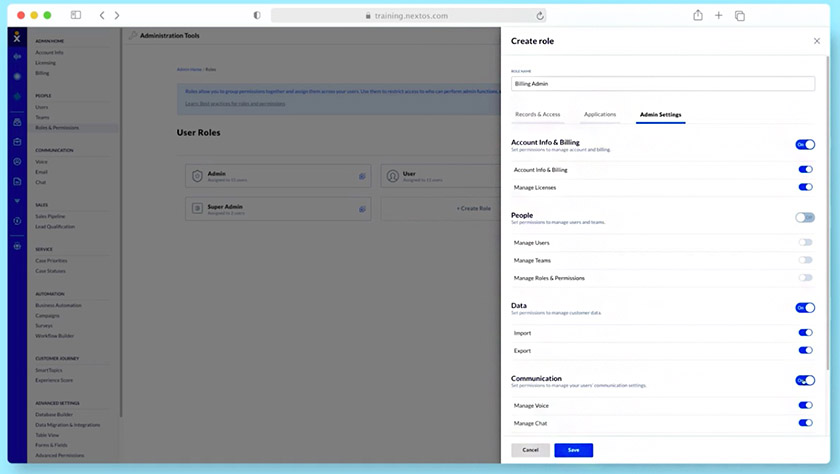
Determine each user’s level of data access by configuring Nextiva role settings. (Source: Nextiva)
Nextiva allows businesses to decide which data points are available to different individuals and teams within the organization. Under the Admin – Role settings, you’ll be able to configure the scope and limitations of user access. For instance, you may turn off the capability to import and export data for certain roles.
VoIP Security Standards
To ensure that your communications are secure, check your chosen business phone system’s data privacy and compliance measures. They should adhere to standards and regulations set by the government and industry associations. These include International Organization for Standardization (ISO), Payment Card Industry Data Security Standard (PCI-DSS), and SOC (Service Organization Compliance) 2.
On top of these, you must be aware of industry-specific standards (for example, the Health Insurance Portability and Accountability Act (HIPAA) for businesses dealing with medical information). Read this comprehensive guide on different types of compliance programs as you compare VoIP providers’ security measures.
Most Secure VoIP Providers
Not all VoIP solutions are equal, as some offer more robust data protection than others. To ensure that your platform is secure, check your phone system’s security certifications and consider how responsive its customer support is. To help you choose, we rounded up some of the most secure VoIP providers:
VoIP Security Best Practices
Data breaches have far-reaching consequences for businesses, including significant financial loss, damaged reputation, and customer trust deficit. Given the range of cybersecurity threats today, it’s important to prioritize protection for commercial data, financial information, and customer databases. To help you strengthen communication security, here’s a summary and reiteration of the best practices you should follow:
Click on the best practices below for more details:
Hackers will have a harder time accessing confidential data when you use strong passwords. Your employees must use passwords with many characters and a mix of letters and numbers, upper and lower case letters, and special characters. Ideally, team members should change these at least every three months. Along with strong passwords, enforce two-factor authentication, as this offers an extra layer of security.
Remind your employees never to connect to free public Wi-Fi. These are unsecured networks, allowing hackers to access your information easily. These cybercriminals are able to monitor your activities while connected to a free Wi-Fi, including the emails and messages sent and online banking credentials keyed in. Instead of connecting to free Wi-Fi, use an unlimited data plan and create a secure personal hotspot for other devices.
A VPN makes an internet connection more secure, as the data traffic goes through an encrypted virtual tunnel. This means the IP address is hidden whenever team members use the internet, protecting organizations against data interception. Through the private network, remote employees are able to access corporate assets safely, regardless of where they are.
Each element in your VoIP infrastructure is vulnerable to cyberattacks. This is why it’s important to inspect the private branch exchange system (PBX), gateways, registrar and locator servers, and IP phones. Examine the phone system’s call state and service content, ensuring that there are no inconsistencies. Even businesses new to this technology and are about to set up their VoIP system must have security audits in their priorities.
Even with the right tools and protocols, your cybersecurity efforts will be in vain when your employees aren’t aware of them. There should be a formal cascading of information to ensure everyone knows how to keep confidential data safe. Your training should involve these aspects:
- Different kinds of cyberthreats and their consequences
- Strict use of authorized devices
- Remote device management
- Backup of important data
- Breach reporting and recovery
Update your training modules as the business grows and more cybersecurity threats emerge. Build a culture in your organization that incentivizes data security compliance and penalizes neglect.
Frequently Asked Questions (FAQs)
Can VoIP be hacked?
Yes, cybercriminals are able to infiltrate business phone systems through various tactics, such as vishing, intercepting networks, and packet sniffing. Once they get into your system, they’ll be able to listen to phone calls, place calls themselves, and obtain commercial information.
Is VoIP or landline more secure?
Neither VoIP nor landline systems are wiretap-proof. However, a landline is the more secure of the two, as it uses circuit switching to establish communication. The path that connects the caller to the recipient is called a circuit and will only transmit data during a live call. In contrast, VoIP uses packet switching, transferring data chunks across different networks. These small bits of data take different routes, making them vulnerable to interception or interruption.
Although VoIP has vulnerabilities, its security systems have become more advanced. For instance, end-to-end encryption and scrambling data into unreadable text keep inbound and outbound calls private. If you’re still considering which phone system to get, read this VoIP vs landline guide.
Does VoIP need a firewall?
Yes, VoIP systems need a firewall to strengthen network security. It tracks incoming and outgoing traffic according to predefined security rules, flagging suspicious activity. It effectively prevents malware that corrupts the system and provides easy access to hackers.
Bottom Line
VoIP systems streamline communications and increase business productivity, but they are vulnerable to cyberattacks when proper security measures are not in place. These attacks cause extensive and sometimes irreparable damage to organizations, which is why information technology security awareness is essential.
To reduce your risk of falling victim to data breaches, familiarize yourself with the most common types of cyberattacks and adopt the best practices for VoIP security. Choose a business phone system with advanced security and compliance certifications.

