Point-of-sale (POS) security protects the computer systems that process debit and credit card transactions. Because point-of-sale systems can contain sensitive data like account numbers, emails, and addresses, hackers target these systems, and a data breach can be costly both financially and reputationally. POS system security does not only apply in-store; POS systems can also be attacked via online stores and through the cloud.
To protect sensitive information, POS systems are typically equipped with a variety of security measures including firewalls, intrusion detection and prevention software, and encryption. However, it’s up to you to make sure your whole system—from employee to network—is as secure as it can be.
This article covers POS security—how it works, the different kinds of security threats, best practices, and costs involved.
How Does POS Security Work?
The ultimate goal of POS security is to protect business data—most importantly customer information that may be accessible via a business’ point-of-sale system. POS security achieves this goal by making information difficult for hackers to see or steal through the following measures:
- Data encryption
- Selectiveness when it comes to usable apps, programs, or integrations
- Restricted access and customizable permissions for users
- Compliance with security standards like the Payment Card Industry Data Security Standard (PCI DSS)
A good POS system from a reputable provider should already include these features as part of its baseline plan. Having said that, there are more steps that business owners can take to maximize their data security. We’ll cover these in our best practices section below, but to provide more understanding, let’s first review what kinds of security threats are out there.
POS Security Threats
There are many recorded cases over the past decade in which restaurant and retail POS systems were targeted to steal payment information or even personal details such as addresses and passwords. In general, almost half of all data breaches occur in the cloud, with organizations using public clouds suffering the most from breaches.
Outdated software, unsecure networks, and unsecure third-party integrations, along with the theft of devices or passwords, sometimes through scams, can leave you vulnerable to attacks. These include malware infections, hardware tampering, brute force attacks, phishing and social engineering, and employee theft.
Expand the sections below to learn more about some common types of threats:
A POS malware attack infiltrates POS terminals or online stores via compromised or poorly-secured systems. The malware searches for payment card data, which is then sent to the attacker unencrypted.
Hackers first get into the system through unprotected databases, program vulnerabilities, or personal access. Then, they install malware that will collect credit card data and other personal information from customers as they make purchases. The data can then be sold on the black market or used to commit identity theft.
POS malware can be very sophisticated and difficult to detect. An attack can often go on quietly for months or years before it’s noticed. Sometimes, a business only finds out from law enforcement investigating another fraud case.
Here are some of the most common types of point-of-sale malware attacks:
- Spyware: This kind of malware installs itself onto a POS system and uploads the stolen data elsewhere. BlackPOS and its derivative Kaptoxa, which were used in the 2013 Target POS breach, are well-known examples.
- Trojans: This software disguises itself as a legitimate program (usually accessed via an email link or file) to get into your system and steal data. For example, in 2014, the Chewbacca Trojan stole more than 49,000 credit cards from 45 retailers in 11 different countries over two months.
- Keyloggers and skimmers: Some spyware steals data by logging keystrokes. Backoff POS and Poseidon both have this capability. This could have been the culprit in 2020, when TrueFire, which offers guitar lessons online, was hacked. Since it does not store payment card information, the info was most likely captured as customers were making payments.
- OAuth hijacking: Open Authentication (OAuth) manages identities and secures online areas across third-party services. This lets users have temporary and secure access tokens—allowing customers to log in to an account using Facebook, for example. While convenient, it can put your account at risk if the other authorization site is hacked. MITRE’s 2022 Common Weakness Enumeration (CWE) Top 25 Most Dangerous Software Weaknesses Report says this was a top threat to businesses in the last year, although it did not mention point-of-sale systems directly.
- Ransomware: This malware attacks your system, usually cutting off company access to computers, email, and customer orders. However, an increasing number of ransomware programs hold your business data hostage and threaten to release public information online if the ransom is not paid. In 2022, The Allison Inn & Spa experienced such an attack, putting information from 1,500 employees and former employees and 2,500 reservations in jeopardy. Nearly 500 million ransomware attacks were detected globally in 2022; these most often happen through desktop sharing and email.
Hackers can tamper with point-of-sale system hardware, such as the card reader, to steal data. This happens with gas pumps, for example, which is why they should be regularly inspected and sealed. However, as self-serve kiosks become more widely adopted by POS providers, this could be another point of risk.

Security seals make it easy to know if a pump has been tampered with. (Image from TydenBrooks)
Hackers can try to guess POS system credentials to gain access and steal data. They use programs to make attempts at hundreds of guesses per second. That’s why it’s important not only to have strong passwords, which reduce the likelihood of being hacked, but to have restrictions on the number of login attempts.
Phishing generally involves scammers sending an email asking for certain information, such as account numbers, in order to transfer money (and then the scammers take money out instead). Social engineering involves manipulating someone into doing something that lets the hacker into the system.
One example is an email, supposedly from a manager or even a CEO, asking the employee to go to a website and purchase gift cards for an event. The scammer then scrapes the payment information. Other scams are similar, with the scammer claiming to be a different employee from within the same company and asking the victim for confidential information. According to the FBI, these scams have cost businesses around the world over $43 billion between 2016 and 2021—and there was a 65% increase in losses between July 2019 and December 2021.
Employees and sales agents are also an area of vulnerability. For example, in Canada, hackers bribed employees at multiple businesses to “borrow” POS devices for about an hour; in reality, the hackers secretly loaded card-skimming software. The result was a loss of over $7 million.
How Do Hackers Gain Access to POS Systems?
Businesses don’t always reveal how a data breach occurred, but in massive breaches, the details come out over time as the retailer works to protect data and settle with customers affected by the breaches. Here are a few examples:
- Bonobos was hacked through an unsecure cloud backup.
- Estee Lauder was hacked through a database that was not password-protected.
- Carter’s was hacked when its third-party vendor Linc shortened Carter’s purchasing and shipping URLs without security precautions.
- Guess was hacked through an unspecified “unauthorized access.”
- Restaurant giant Landry’s was hacked (it believes) when waitstaff erroneously swiped credit cards through the order entry instead of the payment system. Order entry was not encrypted.
- Dickey’s BBQ locations were hacked through outdated magstripe credit card scanners. Hackers can gain access through adjusted credit cards that direct the system to contact a rogue point-of-sale server to download card-skimming software.
- Marriott International was a victim of a social engineering attack, in which an anonymous hacking group tricked an employee into granting them access to its system.
Other areas of vulnerability include hackers tapping in through Bluetooth, especially through remote printing channels; bribing employees to lend them their devices; and finding loopholes in a program.
Just because the incidents above happened to large corporations doesn’t mean that small businesses aren’t also targeted. Incidents like those above are just the ones that get the press. Hence, POS security is an increasingly vital need for small businesses.
Best Practices for POS Security
One PCI DSS requirement is to use antivirus software on all POS systems. POS antivirus software helps protect your system from malware and other cyber threats. However, this software is not enough. Here are other ways you can prevent a point-of-sale security breach:
- Regularly check for card skimmers, cables, or any other tampering. Keep a list or photos of all your terminals with their serial numbers so that you can compare them to the physical terminals and ensure they haven’t been swapped with another device. This is especially important for self-serve kiosks and gas pumps where employees may not be able to constantly monitor the devices.
- Stop allowing card swipe. Hackers can alter credit cards to direct point-of-sale systems to download malware. Use EMV payment tools instead. If you must use card swipe, ensure that all the devices and software programs involved in the transaction have the latest security updates installed. You could also resort to manual keying-in for non-EMV card transactions; while you’ll pay a higher processing fee (often over 3%), you’ll avoid a potential and much more expensive data breach.
- Keep all software up to date with the latest security patches. All kinds of software and components get updated often, which may include new features and patches to any vulnerabilities hackers could exploit. Cloud POS systems, in particular, often have new updates and security patches available for download, so there’s no excuse for not staying up to date.
- Install antivirus and malware protection on your POS device and all devices connected to the network. Antivirus software scans your system periodically and identifies any harmful files or apps on your system. If you’re unsure of which software you should use or how to install it, speak with your POS software account executive.
- Set strict permissions in your software. Managers need access to the back end of your POS system, but you should allow only the permissions that are necessary. Other employees or contractors that need user permissions should have the lowest level that still allows them to perform their role. Keep a list of who has access and what each access level is, so you can trace any breaches and where they occurred.
- Employees at all levels should use strong passwords and change them regularly. The best passwords have at least 12 characters, a combination of capital and small letters, numbers, and characters like ! or &. They can be a phrase (T1m32MK3D0nuts! – Time to make the donuts!) but should not make references to personal information.
- Teach employees email and text security. Malicious attackers typically use email to try to get employee or vendor credentials, but requests may come over the phone or even in person. Employees should be trained on how to identify phishing emails and other common scams, and how to protect their login credentials. For example, no official customer service or IT worker will ask for your username and password. Employees should maintain a mindset of “always verify.”
- Get end-to-end encryption. Most POS systems will include 256-bit level encryption for any data stored on your system, but it’s a good idea to use a payment gateway that also employs end-to-end encryption. This will ensure data is encrypted from the transaction to the gateway.
- Segment your network. An external network is great for customers at a brick-and-mortar store—they get free Wi-Fi, and you’re likely collecting useful data. However, make sure you’ve segmented your network because hackers can easily exploit a system and gain access to payment information. Use an internal network only for payment processing and business-related internet use.
- Keep an eye on point-of-sale activity in your system. Make sure sales and inventory counts make sense and that there aren’t any anomalies in the activity; you should already be checking for discrepancies as part of your regular POS reconciliation process. Also, if your team uses handheld devices to accept payments from customers, make sure you collect them all at the end of the day and lock them up. Employee theft is one concern, but a device could be lost or stolen at some point, and you need to plan for how to prevent this and how to mitigate the damage if it does happen.
- Have a contingency plan. Businesses should be prepared with a predetermined and detailed plan in case their POS system is compromised.
What to Do if Your Business Is Affected by a Data Breach
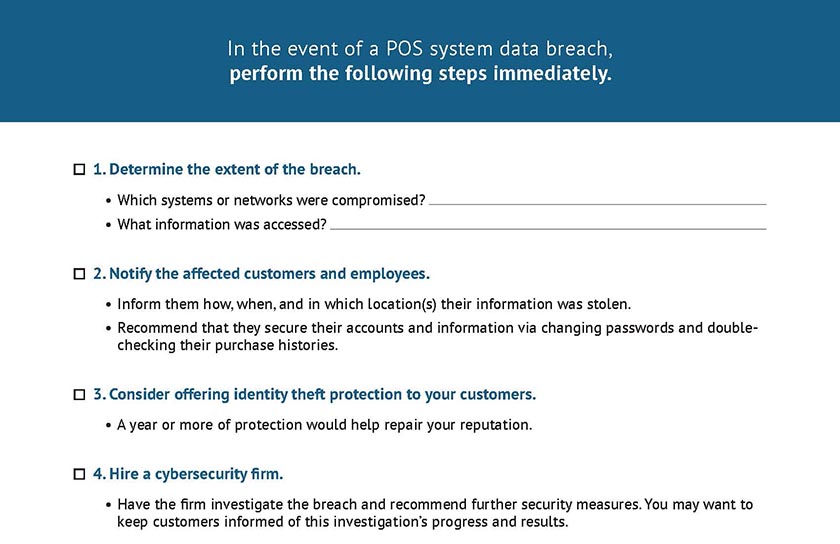
Sometimes, even the best point-of-sale security efforts can’t prevent a data breach. If your business experiences such a breach—which we hope never happens—it is important for your business to react quickly and efficiently. In this case, time really is money as well as reputation. Follow the steps below in case a data breach occurs. You can also use our downloadable checklist.
- Step 1: Determine the extent of the breach. Identify which systems or networks were compromised and what information was accessed. Once the extent of the breach is known, you can start to mitigate the damage.
- Step 2: Notify customers and employees who may have been affected. Let them know how and when they were directly affected (such as cards used during a certain time frame or at a particular store location). Include suggestions for protecting themselves, like changing passwords or checking for purchases they didn’t make.
- Step 3: Consider offering identity theft protection to your customers for a year. This can get pricey but goes a long way toward repairing customer goodwill.
- Step 4: Hire a cybersecurity firm to investigate the breach and implement additional security measures.
- Step 5: Keep track of all communication related to the data breach so that it can be used as evidence if legal action is taken.
- Step 6: Contact the Federal Trade Commission (FTC) law enforcement, and credit bureaus. Law enforcement can help investigate the breach and determine who is responsible. The FTC can provide resources and advice on how to handle the aftermath of a data breach. Credit bureaus can help businesses protect their customers’ credit information.
- Step 7: Contact your insurance company to confirm whether it covers data breaches.
Who Is Responsible for POS Security?
At the end of the day, the data owner (the merchant) is responsible for addressing any data breach. Even if a data breach occurs because of stolen third-party vendor credentials, it’s still your responsibility to make good on the losses, including loss of customer trust.
Click to see a breakdown of security responsibilities by role.
Point-of-Sale Security Costs
A 2022 study by Ponemon Institute found that the average cost of a data breach in the US is nearly $9.5 million—far higher than the global average.
Before COVID-19, 60% of small businesses that suffered a data breach went out of business within six months. That’s why it’s important for businesses to invest in point-of-sale security systems. These systems can help protect your customers’ information and help you avoid costly data breaches.
Worldwide spending on information security exceeded $71 billion in 2022. Most POS companies include security features to help protect POS hardware and software. However, there are extra steps you can take for enhanced security, and they line up with the best practices and tips above.
- Antivirus software: Average costs for antivirus software for your business systems will be about $200 per year. Popular options include McAfee and Norton.
- Firewall: A firewall or router can help protect data transfers on your small business network. These come in a range of prices, but you can expect to pay $100 to $300. Popular options include SonicWall and Cisco.
- Security cameras: Having a camera that covers any areas with point-of-sale terminals or devices is a great way to protect them from physical tampering. Business security systems like SimpliSafe, Vivint, and ADT offer plans anywhere from $9.99 to $59.99 per month.
- EMV chip readers: This is a must. The average cost of EMV readers is anywhere from $50 to $1,000 each. Contact your merchant account provider to make sure you have the latest payment technology.
- Security AI and automation controls: Security AI and automation controls help businesses detect and contain data breaches much faster. These come with monthly fees of $80 to $1,500 per month, but by cutting down detection and reaction time, they reduced data breach costs by 80%.
- Chargeback protection services: Hacking isn’t just about exposing compromised data on the dark web. Criminals also use this information to make fraudulent purchases. While many POS systems and payment providers provide some chargeback protection, you may want to consider a more robust chargeback protection service. Most offer custom pricing, but some have minimum monthly spends of $1,000-plus.
Point-of-Sale Security Frequently Asked Questions (FAQ)
Financial institutions (banks and payment processors) usually bear the brunt of unauthorized charges on debit and credit cards. However, these financial companies may take a merchant to court to cover the cost of protecting customers—for example, Home Depot settled with banks and Target paid a settlement.
No. If you access your POS via the cloud or have an online store on your website, these also need to be secured against hackers. A virus that gets into your computer or server could pull passwords and other information that you are putting into your POS system, or even steal your password to access the system directly.
Mobile devices carry the same vulnerabilities as larger POS systems; they can be attacked by malware or accessed by unauthorized people. Mobile devices are also small and thus easier to steal or lose track of. Apply the same security measures to mobile devices as you do for larger POS systems.
In terms of cybersecurity, open-source POS systems are neither safer nor riskier than other types of POS systems. Viruses, malware, phishing attacks, and other threats are equally present for an open-source POS. Apply the same security measures to these systems as you do for other POS types.
While contactless payment methods lack some of the vulnerabilities inherent to physical payment methods, it is not immune. For example, tampering with the credentials of a mobile or digital wallet could allow a hacker to make fraudulent purchases even in physical store locations. It’s likely only a matter of time before hackers figure out more ways to exploit contactless methods.
Bottom Line
It’s more important than ever for businesses to have comprehensive security protocols in place, particularly where point-of-sale security is concerned. Modern POS systems handle much more than just your business transactions—they also contain sensitive customer information and confidential business data and reports.
Good security means ensuring that all devices used for transactions are up-to-date and properly secured, using strong passwords and authentication methods such as two-factor authentication, and regularly monitoring for suspicious activity. Employees also need to be trained on how to spot potential threats and respond accordingly.