Business communication systems, like voice-over-internet-protocol (VoIP) platforms, store large volumes of sensitive data in the form of texts, faxes, voicemails, and call recordings. To prevent data breaches, service providers follow different types of compliance standards, preserving the integrity of information. The requirements, imposed by the government or industry associations, outline the protocols for collecting, using, storing, and managing sensitive data.
How many types of compliance are there? Basically, there are two: regulatory and corporate. Regulatory compliance, also known as external compliance, refers to a set of rules and practices companies must abide by, as implemented by a regulatory agency. Corporate compliance, or internal compliance, describes the protocols a business enforces within the organization.
Continue reading to explore the common types of compliance for business communication security.
Types of Data Compliance | What It Is | Who It’s For |
|---|---|---|
Health Insurance Portability & Accountability Act (HIPAA) | Seeks to protect patient health information | Healthcare providers and business associates |
Health Information Technology for Economic & Clinical Health (HITECH) Act | Promotes the adoption of health information technology | Healthcare providers and business associates |
Payment Card Industry Data Security Standard (PCI-DSS) | Improves security of payment card transactions | Businesses that handle cardholder data |
Service Organization Control (SOC) | Evaluates security systems and protocols for data stored in the cloud | Companies that use the cloud for communications |
Sarbanes-Oxley (SOX) Act | Enforces financial information security | Businesses listed on the United States stock exchange |
International Organization for Standardization (ISO) | Develops global information security standards | Companies that want to ensure data protection for stakeholders |
General Data Protection Regulation (GDPR) | Sets privacy policies for collecting and using European Union (EU) citizens' data | Businesses operating within the EU and offering services to individuals and businesses in EU |
Customer Proprietary Network Information (CPNI) | Sets limits on the use and sharing of customer information | Telecommunication providers |
Federal Information Security Management Act (FISMA) | Protects sensitive government information and operations | Federal agencies |
Telephone Consumer Protection Act (TCPA) | Prohibits unsolicited calls, texts, and faxes | Telemarketers |
1. Health Insurance Portability & Accountability Act (HIPAA)
The Health Insurance Portability and Accountability Act (HIPAA), the most popular among the types of compliance in businesses, lays out the data privacy and security standards for keeping patient health information (PHI) confidential. The legislation has the following major rules:
- Privacy Rule: Establishes standards for protecting patient information.
- Security Rule: Outlines regulations for securing, transmitting, and maintaining data.
- Breach Notification Rule: Specifies the protocols for handling a security breach.
All companies involved in the healthcare ecosystem must have a HIPAA-compliant business phone system, as they deal with PHI in one way or another. These organizations include billing companies, information technology providers, and even legal and accounting firms. Your partner-VoIP provider must sign a Business Associate Agreement (BAA), a legal contract that specifies their responsibility to comply with HIPAA standards.
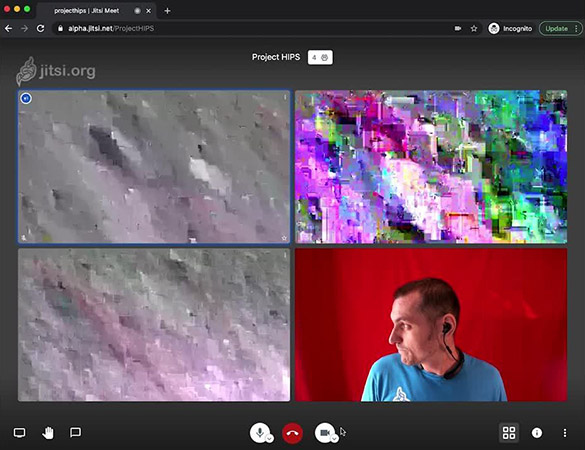
8×8 Jitsi requires an encryption key to view other meeting participants. (Source: 8×8)
8×8 offers a BAA, reassuring businesses that PHI records delivered through phone calls, texts, faxes, and video conferencing sessions are secure and protected. In addition, it uses an extensive audit trail. Its video meeting feature through the Jitsi platform requires users to have an end-to-end encryption key to see other participants and hear the conversation. Check our 8×8 review to learn more about what it offers.
Explore more secure meeting platforms by checking out this list of the best HIPAA-compliant video conferencing solutions. Our top picks include doxy.me, VSee, and Zoom for Healthcare.
2. Health Information Technology for Economic & Clinical Health (HITECH) Act
The Health Information Technology for Economic & Clinical Health (HITECH) Act encourages healthcare providers to adopt electronic health records (EHR) and its supporting technology. It strengthened the HIPAA Privacy and Security Rules by imposing security audits of companies. Under the law, non-compliant businesses will get a maximum fine of $1.5 million. Similar to HIPAA, healthcare providers and their business associates must follow HITECH rules.
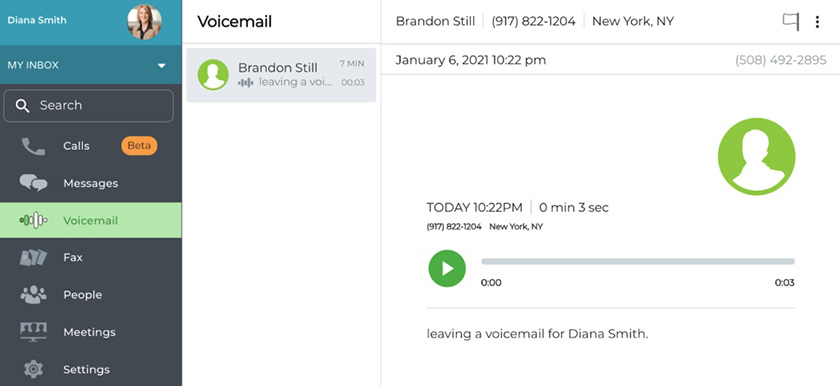
Phone.com offers encryption for health information in voicemails. (Source: Phone.com)
Phone.com is a HITECH-compliant platform, offering encryption for data in motion and at rest. The health information in voicemails and calls are secure in the provider’s servers. In addition, its video meeting solution uses triple Data Encryption Standard (DES), preventing access to unauthorized participants. To determine if this provider fits your business needs, read our Phone.com review.
3. Payment Card Industry Data Security Standard (PCI-DSS)
Aside from health information-related guidelines, there are types of regulatory compliance concerning financial data. The most popular is the Payment Card Industry Data Security Standard (PCI-DSS), which establishes policies for improving the security of debit, credit, and cash card transactions.
It protects account owners from falling victim to data theft and fraud, mandating encryption in transit and at rest for cardholders’ sensitive information, like names, addresses, and credit card numbers. PCI-DSS covers major card brands: Visa, Mastercard, American Express, Discover, and JCB. If your business accepts, transmits, or stores cardholder data, your operations must comply with this data security regulation.
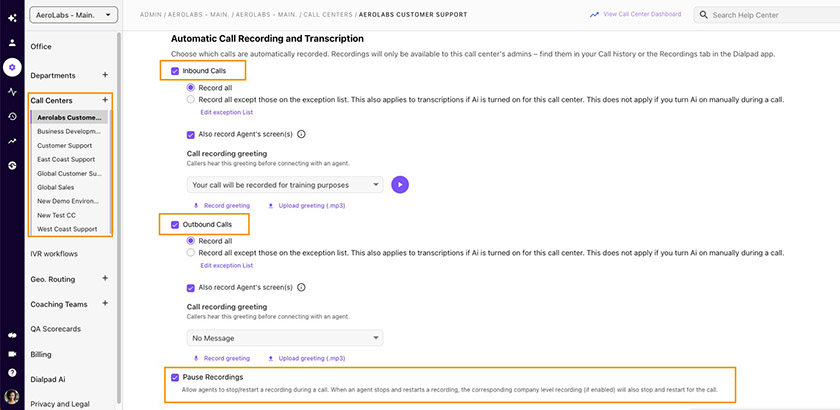
Dialpad lets users pause recording when the caller shares financial information. (Source: Dialpad)
Dialpad’s contact center platform helps companies follow the PCI-DSS regulation by allowing customer service representatives to pause call recordings when taking payment information. Its API also programmatically stops and restarts recordings for users when customers engage with payment systems. This comprehensive Dialpad review will help you decide if this VoIP solution suits your communication requirements.
4. Service Organization Control (SOC)
Service Organization Control (SOC) is an auditing procedure that primarily applies to organizations storing customer data in the cloud. It involves two types of reports produced by independent accountants. Type I describes how your current data security systems align with relevant trust principles, while Type II reviews the operational effectiveness of security systems over a specific audit period.
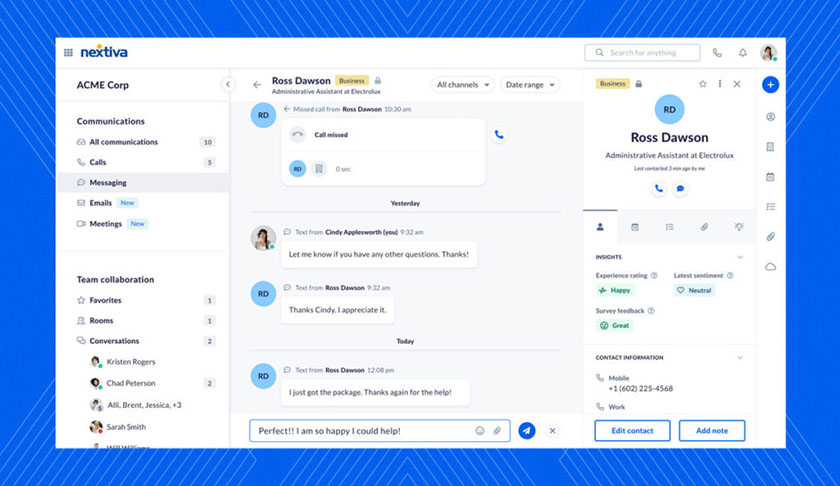
Nextiva’s security measures apply to information stored in the cloud, including chats. (Source: Nextiva)
Nextiva is a business phone system that complies with SOC 2 regulations, ensuring security for data stored in the cloud. Its network security involves call encryption using Transport Layer Security (TLS) and Secure Real-Time Transport Protocol (SRTP) between all endpoints, preventing interception attacks. Learn the pros and cons of subscribing to this VoIP service in this Nextiva review.
5. Sarbanes-Oxley (SOX) Act
The Sarbanes-Oxley Act is a federal law that seeks to protect the public from accounting errors and fraudulent financial practices. It requires public companies to implement internal procedures that ensure the accuracy of financial statements.
The law specifies proper retention and deletion of files containing financial information. For example, customer invoices should be kept for five years. It also regulates employees’ access to specific records based on their roles and responsibilities. If you’re running a publicly traded company, consider partnering with a communications system provider that complies with SOX standards to avoid costly penalties in the future.
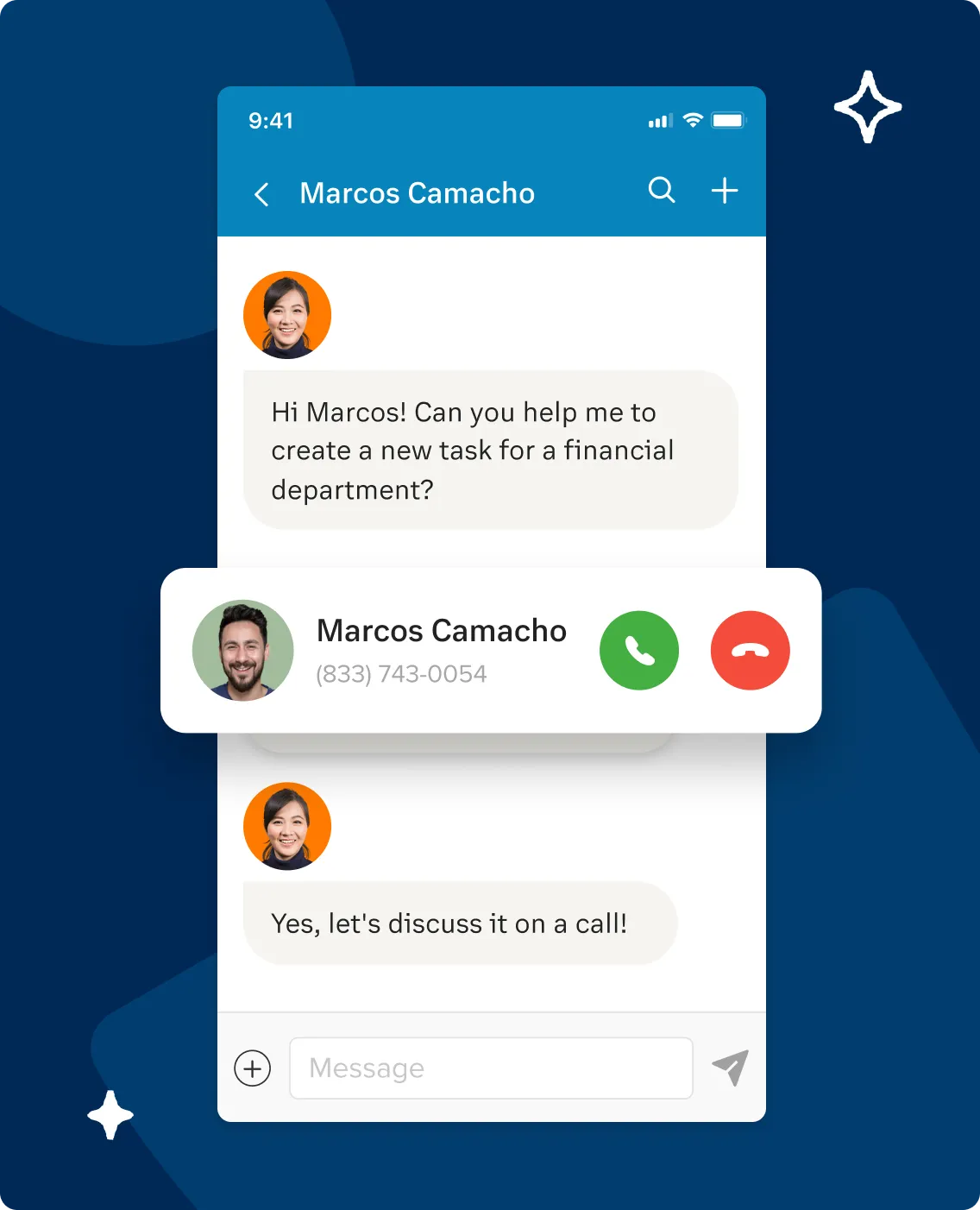
RingCentral follows SOX regulations in keeping financial information safe. (Source: RingCentral)
RingCentral satisfies SOX requirements, putting access controls on financial information. Like other reliable VoIP services, it uses TLS and SRTP encryption between all endpoints. In this RingCentral review, we recommended the VoIP provider to businesses that need advanced call management features. Check out the article to learn if it’s the right solution for you.
6. International Organization for Standardization (ISO)
The International Organization for Standardization (ISO) is known for developing different compliance standards for various industries and activities, including process management, quality control, and health and safety at work. In the case of business communication systems, it introduced various certifications for data security and privacy. The most common are the following:
- ISO 27001:2013: Outlines the requirements for establishing, implementing, maintaining, and improving an information security management system.
- ISO 27017:2015: Specifies guidelines for information security controls when providing and using cloud services.
- ISO 27018:2019: Enumerates the policies for protecting personally identifiable information (PII) in public clouds.
Dialpad has certifications for these ISO standards, ensuring the data shared in its unified communication platform is safe and secure. The VoIP provider offers voice, team messaging, and video conferencing tools.
7. General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) defines privacy and security regulations for organizations collecting European Union (EU) citizens’ data. This applies not only to businesses operating within the territory but also to organizations outside, offering goods and services to consumers or businesses in the EU. If you cater to a regional market, you must satisfy GDPR requirements.
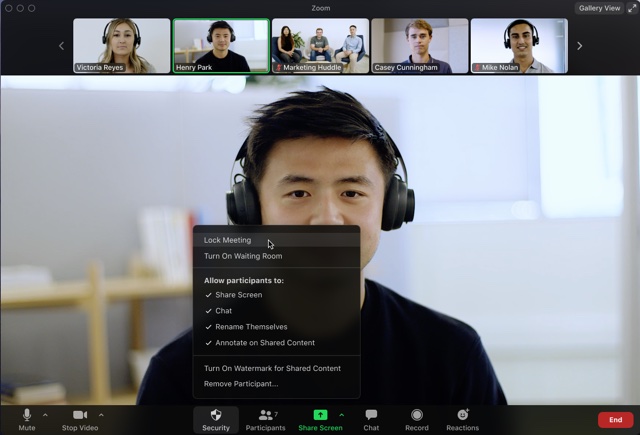
Zoom enables meeting organizers to lock the meeting and restrict access. (Source: Zoom)
Zoom is a business communication platform that satisfies GDPR requirements. Aside from encryption technologies promoting data privacy, the provider conducts data transfer impact assessments when transferring a user’s personal data to a country outside the European Economic Area. If you plan to adopt this tool in your business operations, familiarize yourself with its features by reading our in-depth Zoom review.
8. Customer Proprietary Network Information (CPNI)
The Customer Proprietary Network Information (CPNI) refers to the subscriber information collected by telecommunication services, which includes the time, date, and duration of calls. The Federal Communications Commission CPNI Order defines data use and sharing limits.
The compliance requirements examples include knowing when and how customer service agents disclose call details. It also governs the kinds of information communication companies can share with third-party marketing agencies without getting the consent of subscribers.
Vonage observes CPNI rules, keeping subscribers’ account information confidential. (Source: Vonage)
Vonage is one of the popular VoIP solutions that adhere to CPNI rules, reassuring clients that it doesn’t sell or trade subscribers’ service and usage records with anyone outside of the company. If you want to know the unified communications capabilities of this platform, refer to this comprehensive Vonage review.
9. Federal Information Security Management Act (FISMA)
The Federal Information Security Management Act (FISMA) establishes guidelines for protecting government information and operations. It requires all federal agencies to create, record, and execute a security program that safeguards sensitive data directly handled by the firm and those managed by third-party service providers.
It’s important for government offices to choose a business phone system that follows FISMA rules. One excellent option worth considering is 8×8, as its built-in security tools satisfy the main framework for FISMA compliance, the National Institute of Standards and Technology (NIST) 800-53 R4, ordering federal agencies to develop and employ a data protection initiative.
10. Telephone Consumer Protection Act (TCPA)
The Telephone Consumer Protection Act (TCPA) regulates telemarketing practices, which cover all types of outbound contact via telephone. These include auto-dialed and manual calls, text messages, and faxes. Along with the passing of the law, the National Do Not Call Registry was introduced, banning telemarketers from making unsolicited sales calls.
In 2015, the TCPA Declaratory Ruling and Order clarified specific concerns, including consumers’ right to revoke consent to receive calls and service providers offering robocall blocking. If you regularly conduct telemarketing campaigns, choose a call center system that abides by TCPA guidelines to avoid costly penalties.
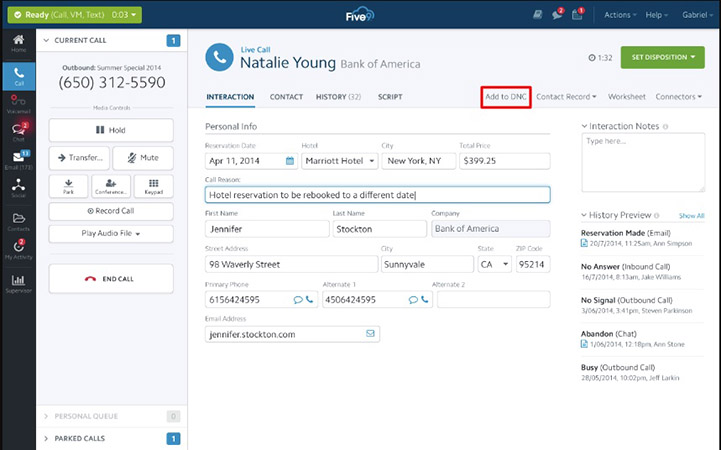
Five9 offers the option to add a contact to DNC to comply with TCPA guidelines. (Source: Five9)
Five9, a reliable contact center platform, partners with legal firms and third-party TCPA compliance vendors to ensure its systems consistently abide by the latest regulations. It works with third-party scrubbing services to check a company’s dialing lists against the Do Not Call registry. We recommended the contact center system to businesses that want an omnichannel platform and a robust auto-dialer.
Why Is Data Compliance Important?
More companies depend on software solutions to facilitate and improve communications with stakeholders. This entails using, sharing, and storing large amounts of data that could easily be the target of cyberattacks. Data compliance regulations compel companies to put the highest standards of information security practices in place and prevent far-reaching consequences that damage organizations and stakeholders.
Here are some specific reasons you should abide by data protection rules:
Data breach incidents leave a bad impression on customers. In contrast, when a company takes the appropriate steps to safeguard information, customers perceive the business as credible and trustworthy. They are more confident to engage in transactions because they know they are safe.
While different types of compliance in business is a big investment, non-compliance to data protection policies costs more. Some regulations carry millions’ worth of penalties. On top of that, many organizations face significant financial loss when a cyberattack targets customers’ personally identifiable information. When you factor in expensive lawsuits, companies experience difficulty recovering.
Data protection laws like GDPR require organizations to know exactly what confidential information to collect and explain how it’s gathered and shared. This practice forces companies to be more intentional in developing a targeted database, which ultimately helps in lead management. With a good grasp of your audience, you’ll craft effective marketing strategies that appeal to them.
Tips on How to Stay Compliant
Compliance isn’t a static project. Rules and regulations change, so you must constantly check if your current practices align with the updated laws. Here are some helpful tips to stay compliant amid policy amendments and revisions:
Have different knowledge sources for regulation updates: business law journals, regulatory agencies’ websites, and compliance seminars. Be part of the local industry associations, as these groups share knowledge about the latest news in the field. Plus, they regularly conduct events like training workshops and conferences that will help you better understand the updates on regulations and keep up with how many types of compliance there are.
When you’re unfamiliar with the language of compliance regulations, you’re prone to overlook important action steps and break the law in the process. To avoid these mishaps, seek the expertise of a legal firm to understand what you need to do. When regulations change, they will be able to clearly explain what’s expected from your organization.
Many software solutions have built-in security solutions that comply with different regulations. By choosing these communication systems, you won’t have to worry about the nitty-gritty of requirements. In line with this, before subscribing to a specific platform and setting up a VoIP system, ask the provider about its security certifications in different compliance categories.
Bottom Line
With the massive amount of information technology threats today, data protection and security should be a top priority for businesses. Review and meet the different types of compliance demands in your industry to earn customer trust, improve communications, and avoid expensive penalties.
To easily keep up with the requirements and create a safe communication environment for stakeholders, go for reliable business phone systems with multiple security certifications. Talk to a VoIP provider today and ask about their data protection measures.