Voice-over-internet protocol (VoIP) security is critical to safeguarding cloud communications against internet-based threats like call tampering, data breaches, and eavesdropping. To minimize the risks, businesses take simple precautions through regular system updates, strict password policies, and virtual private network (VPN) use. Explore other VoIP security tips to help your business strengthen its defense against various VoIP attacks.

Thank you for downloading!
Ooma is a security-centric VoIP provider that uses end-to-end encryption technology to protect company and customer data. The enhanced call-blocking feature lets you automatically add up to 1,000 phone numbers to the block list. Sign up for a 14-day free trial to experience its high-grade security capabilities.
1. Enforce a Strong Password Policy
According to global cybersecurity leader CrowdStrike and its 2024 Global Threat Report, attackers primarily rely on a user’s cloud credentials to initiate network access. This highlights the importance of securing all entry points, including VoIP systems, which require strong passwords to protect your account and communication history against unauthorized access.
Creating a strict password policy ensures hackers cannot access the messages, calls, and customer data stored within employee accounts. A strong password comprises a combination of numbers, special characters, and uppercase and lowercase letters with a length of no less than eight characters. Each work account should have a unique password updated at least every three months.
Consider installing a password manager like 1Password or NordPass on work-related devices to simplify adherence for employees and prevent them from storing their passwords in sticky notes or text files.
VoIP providers offer two-factor authentication (2FA) to significantly reduce unauthorized access to user accounts. Using 2FA requires a second form of verification, making it harder for attackers to compromise accounts even if they have the password.
2. Update Your System Regularly
VoIP providers frequently release updates to ensure your software stays up-to-date with the latest and most advanced security measures. These updates often include security patches that fix bugs and vulnerabilities attackers could take advantage of to compromise your system.
In Ivanti’s 2024 cybersecurity report, software vulnerabilities are the second most common generative AI threat. Attackers use generative AI to exploit your software’s weak points to execute a malicious program or disrupt your operations. In this case, keeping your software updated can improve its defenses against these sophisticated threats.
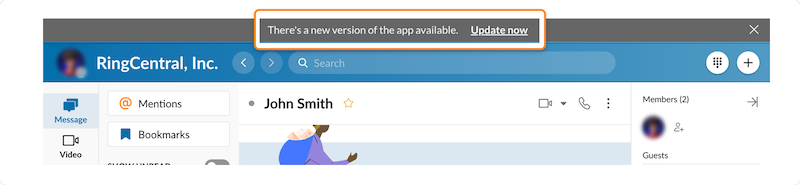
RingCentral displays a banner on top of its desktop app to notify users of a new update. (Source: RingCentral)
3. Find a Secure VoIP Provider
A security-driven VoIP service provider understands the importance of data security and user privacy. In fact, they may have implemented most of the VoIP security best practices already, such as data encryption (at rest and in transit), fraud mitigation, and disaster recovery.
The right VoIP provider should help you meet compliance requirements with government and industry standards. For instance, if you’re seeking a VoIP system for handling patient communications, your VoIP provider must comply with the Health Insurance Portability & Accountability Act (HIPAA), which lays out the standard for handling patient data.
When selecting a provider, choose one that aligns with your specific security needs, especially if your business deals with confidential data. Common features include single sign-on (SSO), multifactor authentication (MFA), and user permissions.
Below are the top VoIP phone systems known for their robust accreditation and encryption capabilities.
Secure VoIP Provider | Monthly Starting Price (per User) | Security Features | Learn More |
|---|---|---|---|
$30 |
| ||
 | $25 | ||
 | $19.99 |
| |
 | $27 | ||
 | $19.99 |
| |
4. Disable International Calling
Disabling international calling on your VoIP system protects you from fraudulent hacking activities like toll fraud. Hackers can use your phone lines during off hours to make high volumes of international calls to premium rate numbers and get a portion of the revenue generated from these calls.
If international calls are necessary for your daily operations, regularly monitor your company’s call activity. Use your VoIP system’s call analytics feature to examine the company’s recent call logs and detect unusual calling trends and activities.
5. Disable Web Interface Use
A VoIP system’s web interface is a hacker’s prime target, aiming to exploit your phone for fraudulent purposes. They can access your web interface remotely via your phone’s IP address, granting them access to key data, including the phone user’s credentials, network settings, and conversation histories.
Turning off your phone’s web interface protects VoIP data from external threats. You can easily re-enable it if you need to adjust your phone settings from your browser.
6. Conduct Security Audits
VoIP systems have a lot of moving parts that significantly affect company security. Conducting routine security audits allows you to detect security gaps, assess VoIP gateways, and take preventative steps to avoid security risks.
A verified security agency will examine every aspect of your VoIP system, including the devices, protocol, software, and network. Security assessment should include cyberattack simulations, application-based security scanning, and patching procedures.
To further minimize VoIP security threats, the auditor will also check whether you have properly configured your VoIP system to comply with industry standards and safeguard against vulnerabilities.
Security audits should not only be limited to your business but must also extend to third-party vendors. According to Ivanti, 53% of organizations have not examined third-party vendors for risks related to artificial intelligence (AI), even though it poses a more significant threat than any other risk factor.
This raises concerns about the potential for the increased risk of AI-powered attacks, making it crucial to audit a software vendor before integrating its services into your system.
7. Install VPN Software
VPNs provide an added layer of security by encrypting internet traffic and masking IP addresses, reducing the risk of cyberattacks or unauthorized system access. It uses an encrypted tunnel that enables users to securely transmit and receive data and secures all traffic wherever the user works.
While VPN use is a must-have for remote work, it also benefits on-site employees accessing external websites. Security threats are heightened for those using public Wi-Fi to check emails and make work-related calls. By installing a VPN, users can protect their online activities from external sources, reducing the risk associated with unsafe browsing.
8. Monitor Call Logs
Reviewing your call logs regularly (i.e., weekly or monthly) can identify unusual calling patterns and establish a basis for how your team uses the VoIP system for normal work activity.
A weekly scan may involve checking for unexpected call volume spikes or calls made after hours, while a monthly scan may concentrate on overall usage patterns. Using the call reporting feature of the VoIP platform can help you establish the baseline usage and the number of calls made over a specific period.
If there are signs of misuse or suspicious activities, the call logs contain valuable information to identify if your VoIP system has been compromised or is being used for unintended purposes. Pay attention to specific metrics, such as odd call times, unrecognized numbers, and unusual voicemail access.
9. Set Up Firewalls
While modern VoIP systems come with numerous security features, they still cannot guarantee complete protection. You’ll need to take additional precautions by securing your entire infrastructure within your network perimeter. Implementing a VoIP-compatible firewall serves as a detection system by blocking unauthorized activities within your network.
A VoIP firewall filters incoming and outgoing voice traffic based on a predefined rule set. It inspects data packets that pass through your phone system and scans for malicious information that might threaten your network.
10. Train Staff on Cybersecurity
VoIP users are the first line of defense against any suspicious activity in your organization.
That is why educating employees about common cybersecurity risks and phone scams is essential, whether they’re using VoIP vs a landline. Unfortunately, many security vulnerabilities arise from user errors, such as using weak passwords, clicking phishing links, or falling victim to social engineering attacks.
CrowdStrike’s 2024 report discovered a growing trend from a group of attackers preying on telecom companies through voice phishing. They’re targeting help desks and attempting to trick support staff into providing passwords or MFA resets of their target accounts.
This incident underscores the importance of VoIP security training, specifically in identifying confidential information and recognizing phishing and social engineering scams. Employees require training on handling these kinds of suspicious requests and identifying these threats at the onset.
Frequently Asked Questions (FAQs)
VoIP systems face many security risks involving unauthorized access, social engineering attacks, and call fraud. One common threat is VoIP-based phishing, where attackers use a spoofed caller ID to convince the call receiver to provide sensitive information.
Distributed denial of service (DDoS) on the other hand, happens by intentionally overloading the server and depriving it of resources to disrupt the phone service, leading to poor uptime, latency, and call quality.
The answer depends on the due diligence performed in setting up and maintaining a network infrastructure. While VoIP systems, like any internet-connected technology, are vulnerable to cyberattacks, effective measures can mitigate these risks. Following the best security practices and committing to the right VoIP service provider can go a long way in protecting your network and company information against different malicious attacks.
Transport Layer Security (TLS) and Secure Real-time Transport Protocol (SRTP) are two of the most secure VoIP protocols that protect data transmission. SRTP is a transport protocol that securely sends data packets between endpoints, while TLS encrypts detailed information like usernames to restrict access from external parties.
Bottom Line
Security threats are inevitable in the VoIP ecosystem, but there are ways to mitigate their impactful consequences. Businesses must implement a comprehensive security strategy if they wish to set up a VoIP system for cloud communications. This strategy should include regular system updates, call log monitoring, and firewall implementation.
Choosing a VoIP provider that prioritizes security can provide peace of mind by ensuring that advanced security measures protect your company’s communications. If this is your priority, RingCentral offers account-level security and end-to-end encryption. Sign up for a 14-day free trial to discover the privacy features they offer.